So much has happened, and in some cases changed, since our April Tech Talk, that we felt our May webinar should be a Tech Talk Bonus edition.
We ...
CSI
SCOTT QUIMBY

So much has happened, and in some cases changed, since our April Tech Talk, that we felt our May webinar should be a Tech Talk Bonus edition.
We ...
CSI
SCOTT QUIMBY

"Been dazed and confused for so long..."
-Led Zeppelin
A former NSA Director said nearly a decade ago that we must start building systems, assuming ...
CSI
SCOTT QUIMBY
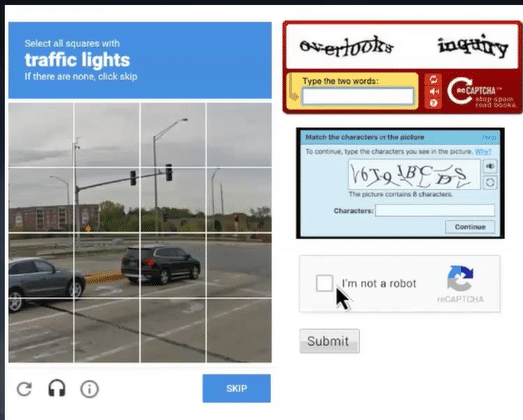
As you present a better and better network defense, the bad guys continue to get more creative in their attacks. A new attack that has shot out of nowhere ...
CSI
SCOTT QUIMBY

"The best offense is a good defense."
-Author Unknown
"The best defense is to go on offense."
-Scott Quimby
If you have been reading our Tech ...
CSI
SCOTT QUIMBY

This exciting session will be led by Scott Quimby, CISSP, Senior Technical Advisor at Acture/CSI, and Larry Lanigan, Site Leader at Acture with 17 years ...
CSI
SCOTT QUIMBY
We are excited to invite you to an exclusive cybersecurity webinar recording led by industry experts at Blackpoint Cyber. This is your opportunity ...
CSI
SCOTT QUIMBY

MITRE is a not-for-profit organization that operates federally funded research and development centers (FFRDCs) to provide technical expertise and innovative ...
CSI
SCOTT QUIMBY

I am sitting at my desk doing what I love—training Acture/CSI's next generation of engineers. I am teaching them about Active Directory theory and operations.
I ...
CSI
SCOTT QUIMBY

Today is a flash drill exercise.
The Superintendent just told you that a retiring employee went rogue on the last day of school and sent a defamatory ...
CSI
SCOTT QUIMBY

Acture/CSI has been going at a dizzying pace. I counted 16 online and in-person events for 2024, plus NYSCATE. Then you add all the Acture Solutions events. ...
CSI
SCOTT QUIMBY

I am sticking you with real work for Spring Break.
My list is very short.
I need you to update, patch, and scan your servers and endpoints
...
CSI
SCOTT QUIMBY

I have a chronic issue with people's ability to close doors securely. The issue is at home, and it spans all ages. I am constantly finding sliding doors ...
CSI
SCOTT QUIMBY

Today is a flash drill exercise.
The warm weather has arrived. It is Thursday afternoon of Memorial Day weekend, and the district gave back an unused ...
CSI
SCOTT QUIMBY

"Now, did you read the news today?
They say the danger's gone away.
But I can see the fires still alight
They're burning into the night."
-Genesis, ...
CSI
SCOTT QUIMBY

Do you know how many inactive accounts you have on your network? I know this can be a difficult number to determine sometimes.
For most of you, Microsoft ...
CSI
SCOTT QUIMBY

Today is a flash drill exercise.
You are experiencing the blizzard of 2025.
The Governor and County Executive have declared a state of emergency.
The ...
CSI
SCOTT QUIMBY

"And now for something completely different."
-Monty Python's Flying Circus
If you have been in the industry for a while, you have heard the warning, ...
CSI
SCOTT QUIMBY

"It Got Weird, Didn't It?"
-Austin Powers: The Spy Who Shagged Me
I just attended the Huntress Security Event in NYC. It was at the Spy Museum on 8th ...
CSI
SCOTT QUIMBY

"This is the end, beautiful friend. This is the end."
-Jim Morrison of The Doors
October 14, 2025, marks the end of the line for our tried-and-true, ...
CSI
SCOTT QUIMBY

I wanted to remind you that "Hacker's Holiday Hours" will start as you wind down for the Christmas break. Last year, I got a call from the SOC on the ...
CSI
SCOTT QUIMBY
We are thrilled to extend our invitation to you for an exclusive Cocktail Party hosted by Acture Solutions! This will be a fantastic opportunity to network ...
CSI
SCOTT QUIMBY

There has never been a more important time for a comprehensive cybersecurity implementation plan. Consider this: On average, US schools lose $500K daily ...
CSI
SCOTT QUIMBY
It seems like Cyber Attacks are happening everywhere these days. Whether it’s a national news report of an attack against a company that has your credit ...
CSI
SCOTT QUIMBY
LAPS is a powerful security tool built into Windows that you can use to secure local administrator accounts on your organization's workstations and mitigate ...
CSI
SCOTT QUIMBY
"School's out for summer."
-Alice Cooper, 1972
School's out for the summer. By the time you read this, I hope my son graduated and is on his way ...
CSI
SCOTT QUIMBY
I spent the day today at the soccer field for the championship games of the local town soccer season. My daughter's team came in third place, winning ...
CSI
SCOTT QUIMBY

Today’s Internet and network security environment differs greatly from just a few short years ago. As we’ve discussed, legacy tools, basic firewalls, ...
CSI
SCOTT QUIMBY
I have a confession to make.
My wife is mad at me.
She insists that I have been negligent about cleaning out the hallway closet. It is small, stuffed, ...
CSI
SCOTT QUIMBY
"I wanna be a lifeguard. I want to guard your life..."
-Blotto 1979
Three of my kids are certified lifeguards. Two have the elite Ellis Lifeguard certification ...
CSI
SCOTT QUIMBY
School's out for the summer.
My son graduated high school.
The 4th of July is our country's 247th birthday.
It is time to make some noise!
Besides ...
CSI
SCOTT QUIMBY

"None shall pass."
-The Black Knight, Monty Python, and the Holy Grail
We continue to see attacks from misconfigured VPNs. Today I want to focus on ...
CSI
SCOTT QUIMBY
Every year, we hear about the Chinese New Year, the animal featured that year, and its significance.
With the start of the new school year, I would like ...
CSI
SCOTT QUIMBY
I read an article today in which a judge declared that Google monopolized search.
Well, that is a big duh!
How long did it take the government to ...
CSI
SCOTT QUIMBY

We are excited to partner with NYSCATE to bring you this important upcoming webinar!
New York State K-12 school districts must comply with EdLaw 2-d, ...
CSI
SCOTT QUIMBY

Cyber risk is growing every day. CSI wants to get you the information you need to know. We invite you to spend a day learning about the cybersecurity ...
CSI
SCOTT QUIMBY

Great News!!
The Federal Communications Commission (FCC) has announced the opening of the Cybersecurity Pilot Program application window for K-12 schools ...
CSI
SCOTT QUIMBY

Exploring the Benefits of Digitalization
Digital transformation is no longer an option. It’s a necessity for school districts aiming to thrive in ...
CSI
SCOTT QUIMBY
I stare at the Paladin Sentinel Monitoring Console every morning and see what happened with our monitored servers and networks overnight. I see many patterns ...
CSI
SCOTT QUIMBY

At 5:30 am one morning, I was awoken by the sound of fire trucks. My neighbor's house diagonally behind my house was on fire. The fire department promptly ...
CSI
SCOTT QUIMBY

A few years ago, there was a very public cyber insurance denial case. As I understand it, the business contracted with Travelers for cyber insurance. ...
CSI
SCOTT QUIMBY

It is Tuesday at 12:29 a.m., at the end of Labor Day weekend. I am driving back from Westchester County Airport, having just flown in from Charlotte, ...
CSI
SCOTT QUIMBY

"Reality is merely an illusion, albeit a very persistent one."
-Albert Einstein
"You live in a world of illusion Where everything's peaches and ...
CSI
SCOTT QUIMBY

I remember those days when the Apple folks would scoff at having to have antivirus. Macs were superior, and Windows devices had all those problems.
The ...
CSI
SCOTT QUIMBY
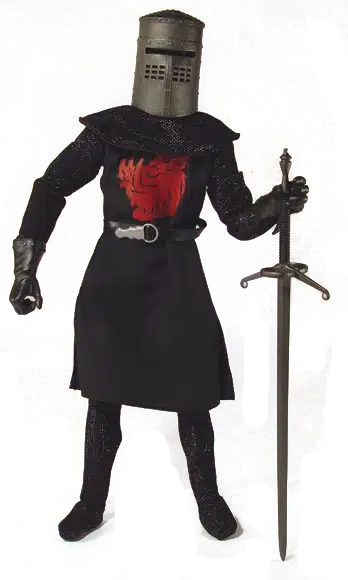
Today’s cyber landscape feels a lot like this picture. Anyone who uses a device connected to the internet is under threat. You never know when that ...
CSI
SCOTT QUIMBY

You arrive at work tomorrow and are greeted by the news that a cyber-attack has compromised your district’s network, and the network is unavailable. ...
CSI
SCOTT QUIMBY

I read the other day that today is "Worldwide Backup Awareness Day." I have no idea who declares these days. I am guessing you already know you should ...
CSI
SCOTT QUIMBY

Here is my "Top 5" list to up your cybersecurity defenses:
Make sure that whatever your current endpoint protection strategy is, it is 100% in place. ...
CSI
SCOTT QUIMBY

There is a new, growing attack surface that is becoming increasingly dangerous to your network operations—the cloud, specifically your Google Apps or ...
CSI
SCOTT QUIMBY
Welcome back!
This summer flew by, and my summer vacation seems like a distant memory. In my 44 years of helping schools open for the new school year, ...
CSI
SCOTT QUIMBY

A year ago, my very short wife sat in a restaurant during March Madness on a bar stool that was too tall for her. The result was that while getting down ...
CSI
SCOTT QUIMBY
You already know that "all" in security protection is vitally important. You need all your endpoints and servers protected with something. Hopefully, ...
CSI
SCOTT QUIMBY

We live in interesting times and continue to face unique challenges to keep your school district safe and stable so teachers can teach, students can learn, ...
CSI
SCOTT QUIMBY
You have probably heard of the AT&T breach by now. Reports describe it as the largest breach in history with serious national security consequences.
AT&T ...
CSI
SCOTT QUIMBY
"Trust but verify."
-President Ronald Reagan, December 8th, 1987, at the Intermediate-Range Nuclear Forces (INF) Treaty Signing
I watched a presentation ...
CSI
SCOTT QUIMBY
It has been a rough two weeks for many of us who support technology for our school districts.
We have experienced the worldwide meltdown of CrowdStrike ...
CSI
SCOTT QUIMBY
During the Pandemic, Threat Actors had a field day using phishing and SEO poisoning to attack users.
We are in the same climate again with the horrible ...
CSI
SCOTT QUIMBY
Gabe, Lisa, and I attended the annual CyberSecurity Summit at my Alma Mater, Marist College. Back in the day, at the beginning of the IBM/Marist Joint ...
CSI
CSI

Acture/CSI is growing again. We are looking for high-quality individuals to work with our service delivery team.
Please search our Acture/CSI online ...
CSI
SCOTT QUIMBY

CISA in their January and August 2023 Bulletins again called out some of the most important ways that schools can protect themselves from cyber attacks. ...
CSI
SCOTT QUIMBY

As we attempt to harden our networks and strengthen our passwords, I wanted to bring up something again I have talked about in various settings. Password ...
CSI
SCOTT QUIMBY
Recently it was worldwide "change your password" day!
I have a few thoughts.
If you attended the CSI CyberSecurity event in December, you heard the ...
CSI
SCOTT QUIMBY

Would you be comfortable giving your plumber the key to your house so he/she can come in at any time to fix anything they might feel is amiss? The answer ...
CSI
SCOTT QUIMBY
We live in interesting times and continue to face some very unique challenges to keep your school district safe and stable so teachers can teach, students ...
CSI
SCOTT QUIMBY
We live in interesting times and continue to face some very unique challenges to keep your school district safe and stable so teachers can teach, students ...
CSI
SCOTT QUIMBY
Join us, as Scott discusses his latest "Tech Tidbits" including updates on security and industry news since we last got together.
Watch ...
CSI
SCOTT QUIMBY
Join us, as Scott discusses his latest "Tech Tidbits" including updates on security and industry news since we last got together.
Watch it here
×
Please ...
CSI
SCOTT QUIMBY
Tech Tidbits - Scott's updates on security, updates, and industry news since we last got together.
Harden your endpoints as part of your overall ...
CSI
SCOTT QUIMBY
Tech Talk Part II will be a special session on email. We will talk about the following:
Reading email headers. Every time something bad comes into ...
CSI
SCOTT QUIMBY
Bob will be discussing infrastructure upgrades covering hardware "end of life" planning over the next few years as well as new switch management alternatives ...
CSI
SCOTT QUIMBY
Part one of CSI's Fall 2022 technical discussion is oriented toward K-12 public school district technical staff featuring technical and security news, ...
CSI
SCOTT QUIMBY

Happy Spring!
As Spring break looms for most of you, I once again need to be a killjoy and remind you of a stark reality.
Whenever you and your team ...
CSI
SCOTT QUIMBY

I know of three CIAs:
The Central Intelligence Agency (CIA)
The Hudson Valley's Culinary Institute of America (CIA)
The Triad of Information ...
CSI
SCOTT QUIMBY

Please join us on Wednesday, March 8th, as Scott Quimby delivers a special update addressing the current K-12 cybersecurity challenges, NIST Cybersecurity ...
CSI
SCOTT QUIMBY

It seems like Cyber Attacks are happening everywhere these days. Whether it’s a national news report of an attack against a company that has your credit ...
CSI
SCOTT QUIMBY

Everyone knows the adage “No one is perfect”. Unfortunately for anyone with a computer network, the bad actors who want to infiltrate your system ...
CSI
SCOTT QUIMBY
Join Cisco and CSI for a very special upcoming webinar. We will be joined by several specialists from Cisco (including Cisco Talos) who will discuss the ...
CSI
SCOTT QUIMBY

Scott Quimby discusses the following:
Reading DMARC reports - In preparation for achieving DMARC Quarantine status, Scott will walk you through reading ...
CSI
SCOTT QUIMBY

My wife works for a multi-billion dollar hospital network you all will know. Every time she signs into their mandated VPN and MFA solution she curses ...
CSI
SCOTT QUIMBY

New York State K-12 school districts must follow EdLaw 2-d. We all know that is easier said than done. It is hard work with limited staff and limited ...
CSI
SCOTT QUIMBY

Microsoft has tried hard to increase awareness of "pass the hash" attacks. They have been patching, but the threats keep coming. Back in April Microsoft ...
CSI
SCOTT QUIMBY
The first session will be led by Scott Quimby, CISSP, Vice President and CTO of CSI. He will focus on "Tech Tidbits" providing timely informational updates ...
CSI
SCOTT QUIMBY

Join us, as Jeff Pigula, CSI Senior Network Engineer (Cisco CCNA and CC-NSF) will be discussing the changing world of PoE power management - what you ...
CSI
SCOTT QUIMBY

March marks the month that I have been working with technology professionally for 46 years! It seems like yesterday that as a 16-year-old high school ...
CSI
SCOTT QUIMBY

This week, I would like to talk to you about Malware Defenses. This topic is in the NIST Detect and Protect categories.
Antivirus has been around for ...
CSI
SCOTT QUIMBY
![CSI's Tech Talk-Wednesday, April 17th [IN PERSON] Save your seat today!](https://www.csiny.com/wp-content/uploads/2018/03/3769767882_01.jpg)
We are pleased to announce our upcoming Tech Talk/SYSOP will be IN PERSON on Wednesday, April 17th! This is the first in-person Tech Talk since the ...
CSI
SCOTT QUIMBY

'Those who cannot remember the past are condemned to repeat it'
-George Santayana From his work; Life of Reason, Reason in Common Sense 1905
You have ...
CSI
SCOTT QUIMBY

What would you do if you came into school tomorrow and were told that all your District’s data had been corrupted? Your next step would be to check ...
CSI
SCOTT QUIMBY

Now that I work in a hybrid mode, it is always so annoying when I go to the office and forget my office keys. I have to ask someone to let me into my ...
CSI
SCOTT QUIMBY
It has been reported that when attackers breach your network, they often first go after your backups in an attempt to corrupt them so that you have no ...
CSI
SCOTT QUIMBY

On behalf of the entire CSI team, I want to wish you a very happy holiday season. Hopefully, you can enjoy some downtime with friends and family and maybe ...
CSI
SCOTT QUIMBY

Have you ever started looking into a complex topic, and been overwhelmed by all the details of what is involved? Not only is it hard to understand, but ...
CSI
SCOTT QUIMBY

We have had several districts come online with CSI's CyberCNS Vulnerability Advisory Service. That has given me a substantial amount of vulnerability ...
CSI
SCOTT QUIMBY

Cyber risk is growing every day. In 2022 K-12 education was the single most targeted industry for ransomware. CSI wants to get you the information you ...
CSI
SCOTT QUIMBY

From all of us at CSI we wish you a Happy Thanksgiving.
We are thankful for all of you. We are proud that we first started working with K-12 school ...
CSI
SCOTT QUIMBY

One thing that became very clear to me over the summer is that the bad guys are being very intentional in formulating attacks against your districts and ...
CSI
SCOTT QUIMBY

Children spread viruses of all sorts – at home and in the classroom. It is just something you come to expect. Did you know they can also spread Cyber ...
CSI
SCOTT QUIMBY
Cyber risk is growing every day. In 2022 K-12 education was the single most targeted industry for ransomware. CSI wants to get you the information you ...
CSI
SCOTT QUIMBY

It is already a weird summer for me. I normally go to Acadia National Park right about now and enjoy the Maine weather. (It is so weird that NY has Maine ...
CSI
SCOTT QUIMBY

How do you intend to block lateral movement if an attacker has made it into your network?
In looking at recent ransomware attacks there are some consistent ...
CSI
SCOTT QUIMBY

Today's assignment is both easy and hard - Look through your password database, talk to your staff, and identify all the vendors and devices that are ...
CSI
SCOTT QUIMBY

When it comes to improving network security, the question asked is usually “Can we afford it?” But with Cyber Crime evolving every day, the question ...
CSI
SCOTT QUIMBY

Your assignment this week is to evaluate the printers on your network.
The reality is that network-enabled printers are a serious security threat to ...
CSI
SCOTT QUIMBY

VMware has published a security advisory regarding a critical out-of-bounds write vulnerability (CVE-2023-34048) that has been fixed in the latest updates ...
CSI
SCOTT QUIMBY

As the school year winds to a close, preparation begins in earnest for summer projects. Many departments within your district will be planning new additions ...
CSI
SCOTT QUIMBY

The rate of cyber-attacks has significantly increased over the past few years. Districts of all sizes are at risk of becoming victims of them, which is ...
CSI
SCOTT QUIMBY

Today we continue with our series discussing the highest priority cybersecurity steps as identified in the January 2023 CISA published report “Partnering ...
CSI
SCOTT QUIMBY

Last week I discussed the need to have all passwords minimally 12-18 characters to remain safe. While that is an absolute security requirement, we all ...
CSI
SCOTT QUIMBY

Everyone has heard about the cyber attack on casino giants MGM and Caesars Entertainment in September 2023. It is alleged that the attack on MGM was done ...
CSI
SCOTT QUIMBY

Today we continue with our series discussing the highest priority cybersecurity steps as identified in the January 2023 CISA published report “Partnering ...
CSI
SCOTT QUIMBY

Reality Check - Adobe FLASH IS DEAD! THERE SHOULD BE NO FLASH IN YOUR NETWORK!
As I start seeing more and more of these vulnerability scans from districts ...
CSI
SCOTT QUIMBY

Today we continue with our series discussing the highest priority cybersecurity steps as identified in the January 2023 CISA published report “Partnering ...
CSI
SCOTT QUIMBY

Today we continue with our series discussing the highest priority cybersecurity steps as identified in the January 2023 CISA published report “Partnering ...
CSI
SCOTT QUIMBY

Your district network is complex. You have lots of VLANs. You have lots of servers and endpoints. Lots of UPSes, switches, and on and on. Then you have ...
CSI
SCOTT QUIMBY

Add the last "S" for security.
I remember the old mattress commercials. You left the last "S" of the phone number for savings. In our world, we need ...
CSI
SCOTT QUIMBY

The FBI has just issued a warning that cyber criminals are using search engine fake ads to launch cyber-attacks.
Their suggestions are excellent.
You ...
CSI
SCOTT QUIMBY

I am not a basketball person, but it is said that the late Kobe Bryant had one of the best work ethics in all of sports spending endless time practicing ...
CSI
SCOTT QUIMBY

We live in interesting times and continue to face some very unique challenges to keep your school district safe and stable so teachers can teach, students ...
CSI
SCOTT QUIMBY

Today we continue with our series discussing the highest priority cybersecurity steps as identified in the January 2023 CISA published report “Partnering ...
CSI
SCOTT QUIMBY

On any team, there is someone who has the vision and sets goals, and there is someone on the ground who makes sure those things happen. No team can be ...
CSI
SCOTT QUIMBY

As we mentioned in our last bulletin, in January 2023 CISA published a report “Partnering to SafeGuard K-12 Organizations ...
CSI
SCOTT QUIMBY

We have been talking a lot in these bulletins about the increase in Cybersecurity incidents and what can be done to mitigate that risk. Congress also ...
CSI
SCOTT QUIMBY

I am sitting here at 6 a.m. doing the morning review of all our Paladin Sentinel Monitoring school districts. The storm came overnight and there were ...
CSI
SCOTT QUIMBY

Today it seems everything is connected to the internet in some way. At home, you have doorbells, garage doors, TVs, and a myriad of other things. School ...
CSI
SCOTT QUIMBY

Today's Tidbit should be quite simple once you get going. NIST requires data to be encrypted in transit and at rest.
Probably you have a number of staff ...
CSI
SCOTT QUIMBY

Imagine you’ve been hit by a Cyber Attack. Your network is locked by ransomware and all your data is compromised. What ...
CSI
SCOTT QUIMBY

In August of 2021, CISA added "Single Factor Authentication" to its list of practices it considers "exceptionally risky" as it exposes you to an "unnecessary ...
CSI
SCOTT QUIMBY

I watch a lot of Cybersecurity presentations. Ransomware is on everyone's lips as a major concern. Here are two interesting tidbits of information.
...
CSI
SCOTT QUIMBY

Perhaps you’ve heard the story of the young girl walking along the seashore, who noticed hundreds of starfish that had washed up along the beach with ...
CSI
SCOTT QUIMBY

Today’s Internet and network security environment is very different from what it was just a few short years ago. As we’ve discussed, legacy tools, ...
CSI
SCOTT QUIMBY

Have you ever been part of a group where a leader has not been clearly identified? It takes twice as long to get anything done and arguing and conflict ...
CSI
SCOTT QUIMBY

In October 1993 I was sitting in a van in dusty Nmanga, Kenya. Nmanga was the only legal border crossing between Kenya and Tanzania. It is next to Amboseli ...
CSI
SCOTT QUIMBY

Everyone knows the adage “No one is perfect”. Unfortunately for anyone with a computer network, the bad actors who want to infiltrate your system ...
CSI
SCOTT QUIMBY

Last week we talked about how one weak link can open the door to a Cyber Incident. We discussed the weak link of old, unused user IDs remaining in your ...
CSI
SCOTT QUIMBY

There is a new critical security issue that affects web browsers as well as other software that use something called libwebp. This feels a whole lot like ...
CSI
SCOTT QUIMBY

We have all heard the phrase "A chain is only as strong as its weakest link". When it comes to Cyber Security that phrase is all too true. Sometimes ...
CSI
SCOTT QUIMBY

Last weekend my youngest daughter started a new baton program on Saturday mornings. Sitting there I realized I have been taking at least one of my four ...
CSI
SCOTT QUIMBY

In August of 2021, CISA added "Single Factor Authentication" to its list of practices it considers "exceptionally risky" as it exposes you to an "unnecessary ...
CSI
SCOTT QUIMBY

Far too often we hear people say “I don’t need to worry about security tools and training, I have Cyber Insurance”. While this doesn’t apply to ...
CSI
SCOTT QUIMBY

Whether you are a sports enthusiast, a volunteer, or part of a work team, you have experienced first-hand the importance of good teamwork. We have all ...
CSI
SCOTT QUIMBY

Business Email Compromise (BEC) has become a security buzzword. It simply means using email to attack and gain access to your network. *Phishing* or *Spearphishing* ...
CSI
SCOTT QUIMBY

Welcome back!
It was a very busy summer for all of us. Summer and the start of the school year felt much more "normal" to us.
Putting my parent ...
CSI
SCOTT QUIMBY

This week I would like to talk to you about Malware Defenses. This topic is in the NIST Detect and Protect categories.
Antivirus ...
CSI
SCOTT QUIMBY

As mentioned in last week’s Tech Tidbit, we have begun a new series of weekly bulletins sent to School Business Officials giving ...
CSI
SCOTT QUIMBY

This week I’d like to talk a little bit about the NIST Category - Recover. According to NIST, the Recover Category “identifies ...
CSI
SCOTT QUIMBY

In last week’s email, we talked about the third NIST Cybersecurity Framework category – Detect. ...
CSI
SCOTT QUIMBY

In last week’s email, we talked about the second NIST Cybersecurity Framework category – Protect. ...
CSI
SCOTT QUIMBY

In last week’s email, we talked about the first NIST Cybersecurity Framework category – Identify. This ...
CSI
SCOTT QUIMBY

In last week’s email, we talked about what the NIST Cybersecurity Framework was, how it ...
CSI
SCOTT QUIMBY

Your district is faced with ever-increasing threats, pressures, and regulations. The list is endless. K-12 Cyberattacks continue ...
CSI
SCOTT QUIMBY

I learned to drive "on the wrong side of the road" on a Monday morning in downtown London. I hit my first object in about 50 feet when I ran over ...
CSI
SCOTT QUIMBY

Late in the afternoon on a Friday, I created a bit of a scare for those of you who are part of our Paladin Sentinel monitoring system. I was doing my ...
CSI
SCOTT QUIMBY

We have recently been approached by many school districts to talk to their district office staff and in some instances their faculty about phishing and ...
CSI
SCOTT QUIMBY

If you subscribe to our Paladin Sentinel monitoring service, hopefully, you know that either myself or one of our technical staff actively sweeps through ...
CSI
SCOTT QUIMBY

Occasionally the SentinelOne agents included in our CSEDR offering are operating but show a red "x" denoting that the agent is operational, ...
CSI
SCOTT QUIMBY

We have a new technology coming online with all the popular web browsers. It is called DNS over HTTPS or DoH. The concept is instead of using your ...
CSI
SCOTT QUIMBY

We all understand the scourge of Ransomware. It is debilitating. Even in the best case, it consumes a huge amount of time to recover. However, ...
CSI
SCOTT QUIMBY

“You don’t have to run faster than the bear to get away. You just have to run faster than the guy next to you.”
― ...
CSI
SCOTT QUIMBY

It is already a weird summer for me. I normally go to Acadia National Park right about now and enjoy the Maine weather. (It is so weird that NY has Maine ...
CSI
SCOTT QUIMBY

I was watching a panelist discussion post-mortem discussing firsthand knowledge of 25 major ransomware-style breaches. One of the panelists was an award-winning, ...
CSI
SCOTT QUIMBY
Cyber Security has grown into an issue that needs to be addressed by everyone in a school district, not just by the Director of ...
CSI
SCOTT QUIMBY

In August of 2021, CISA added "Single Factor Authentication" to its list of practices it considers "exceptionally risky" as it exposes ...
CSI
SCOTT QUIMBY

Last weekend my youngest daughter started a new baton program on Saturday mornings. Sitting there I realized I have been taking ...
CSI
SCOTT QUIMBY

How do you intend to block lateral movement if an attacker has made it into your network?
In looking at recent ransomware attacks ...
CSI
SCOTT QUIMBY

I am sitting here at 6 am doing the morning review of all our Paladin Sentinel Monitoring school districts. The storm came overnight ...
CSI
SCOTT QUIMBY

Add the last "S" for security.
I remember the old mattress commercials. You left the last "S" of the phone number for savings. ...
CSI
SCOTT QUIMBY

In today’s school environment, everyone and almost every piece of equipment talks to the internet and run on your network. Your HVAC system, ...
CSI
SCOTT QUIMBY

"I am watching you...Always watching"
-Roz Monsters Inc.
For New Year's we once again had a holiday crisis. Fortunately, this wasn't an attack. Microsoft ...
CSI
SCOTT QUIMBY
Please join us *tomorrow - Wednesday, October 12th* for an upcoming webinar focusing on Business Email Compromise. Jason Whitehurst, a cybersecurity professional, ...
CSI
SCOTT QUIMBY

All versions of vSphere prior to version 7.0 are about to be retired from support
I would like to make you ...
CSI
SCOTT QUIMBY

"None shall pass"
-The Black Knight "Monty Python and the Holy Grail"
Today I would like to challenge you ...
CSI
SCOTT QUIMBY

A few years ago, in a Tech Talk I talked about a major college that suffered a complete network lockout due to a soda machine ...
CSI
SCOTT QUIMBY

The first line of email defense is a properly formed SPF record
"Paper's Please"
Those words ...
CSI
SCOTT QUIMBY

We always have the Paladin Sentinel Monitoring console up during the day. I am still seeing mass use of the domain administrator account to RDP into ...
CSI
SCOTT QUIMBY

You all may have heard Scott talking about "those ex-NSA guys at Huntress" he talks to. Bob and Scott have been stressing the importance ...
CSI
SCOTT QUIMBY

"Treat your password like your toothbrush. Don't let anyone else use it and change it every six months"
-Clifford Stoll
Password security ...
CSI
SCOTT QUIMBY

I wanted to update you on the Microsoft authentication issues caused by the May patches.
Microsoft has released an "out of band" update ...
CSI
SCOTT QUIMBY
This month we talked about how the Ukraine situation affects the cybersecurity landscape for the US and what it means for network security. ...
CSI
SCOTT QUIMBY

I wanted to update you on the Microsoft authentication issues caused by the May patches.
This only potentially affects Microsoft Domain ...
CSI
SCOTT QUIMBY

Recently I wrote about the increasing vulnerabilities in BIOS/UEFI underneath the operating system and encouraging you to update your devices ...
CSI
SCOTT QUIMBY

Quest has notified us that they have a critical vulnerability. If you use a KACE appliance, please read this information and perform their ...
CSI
SCOTT QUIMBY

"Legends state that Achilles was invulnerable in all of his body except for one heel because when his mother Thetis dipped him in the River ...
CSI
SCOTT QUIMBY

Speaker: Alan Winchester, Chief Development Officer, Caetra.io
Alan Winchester is the Chief Development Officer and creator of CyMetric™. ...
CSI
SCOTT QUIMBY

Mitre Engenuity has released its 2022 fully independent evaluation of 30 of the most common cybersecurity endpoint protection platforms. Why does this ...
CSI
SCOTT QUIMBY

Your techs *should not* be local admins anymore. It is simply too dangerous.
I have personally been a limited user on all ...
CSI
SCOTT QUIMBY

We have to plan to safely ride out storms and other unforseen events
I am fresh off another weekend of power issues with ...
CSI
SCOTT QUIMBY

"War, huh, yeah What is it good for? Absolutely nothing, uh-huh, uh-huh"
-War by Edwin Starr
The world is ...
CSI
SCOTT QUIMBY

How I manage the storm of information and how you can quickly know what I think is important.
A few thoughts on how I manage ...
CSI
SCOTT QUIMBY

Today's NIST Topic is - "Implement a Security Awareness and Training Program"
This is something ...
CSI
SCOTT QUIMBY

"Mind the Gap"
As the war unfolds and these "Hacktivist" Guerillas take their shots at both sides of the fight, the details ...
CSI
SCOTT QUIMBY

“Just when you thought it was safe to go back in the water...”
― Peter Benchley, Jaws
It ...
CSI
SCOTT QUIMBY

Please join us for CSI's Cybersecurity Event, Session Three! We will continue to build the list of actions ...
CSI
SCOTT QUIMBY

Surge protectors need to be banned from your wiring closets
Hi Lisa,
A few thoughts on UPSes and Surge Protectors.
If you need ...
CSI
SCOTT QUIMBY

"I think someone shot a torpedo at us"
-The Hunt for Red October
It started out as an ordinary weekend full of kid's schedules ...
CSI
SCOTT QUIMBY

You can easily block these applications from getting on your endpoints
Here's a quick Tech ...
CSI
SCOTT QUIMBY

"Everyone fears rejection"
-Derek Jeter
It finally happened. I got kicked in the head and rejected.
Here ...
CSI
SCOTT QUIMBY

Keep your browser extensions limited to those you need to support the district and trust
"There ...
CSI
SCOTT QUIMBY

"I am watching you...Always watching"
-Roz Monsters Inc.
For New Year's we once again had a holiday crisis. ...
CSI
SCOTT QUIMBY

Boring Email Formatting = Improved Reliability
We love to use graphics and links in our emails. There are lot ...
CSI
SCOTT QUIMBY

Your technical staff's equipment needs to be the best maintained in the district
Some thoughts on patching your holy of holies.
If ...
CSI
SCOTT QUIMBY

Cybersecurity Event Session Two: The Front Lines of Ransomware
Speaker: Chris Loehr, Co-Founder, Service Provider Partners
Chris ...
CSI
SCOTT QUIMBY

It has been a very frustrating couple of months trying to keep everyone safe and stable. Since the Spring we have been pummeled ...
CSI
SCOTT QUIMBY

I have four quick thoughts for you to ponder
Here are a couple of items that I have been reminded ...
CSI
SCOTT QUIMBY

With school districts now required to adopt the NIST Cybersecurity Framework (CSF) for managing their IT operations, our district ...
CSI
SCOTT QUIMBY

I have something hard that I really need you to do - audit your DNS. It takes a lot of time. It is boring to do. However, it ...
CSI
SCOTT QUIMBY

I heard the other day that the FCC is moving to get more aggressive in getting phone carriers to do all they can do to block ...
CSI
SCOTT QUIMBY

"Breakin' Up Is Hard To Do" - Neil Sedaka 1966
In the last 10 days we talked about the attacks on VCenter and recommended ...
CSI
SCOTT QUIMBY

In August CISA added "Single Factor Authentication" to its list of practices it considers "exceptionally risky" as it exposes ...
CSI
SCOTT QUIMBY

As I have gotten older I have developed claustrophobia. MRI machines are now my nemesis. Fortunately, I have not needed one ...
CSI
SCOTT QUIMBY

Join us for a quick, 30-minute webinar to learn about the potential technology funding available to school districts through ...
CSI
SCOTT QUIMBY

I think by now everyone is officially open. I know some districts locally and in the Northeast had horrific transportation issues. ...
CSI
SCOTT QUIMBY

Back in April, I had sent Bob and Scott's top 3 solutions you should have in place NOW to best protect against ...
CSI
SCOTT QUIMBY

My daughter graduated just from High School. Immediately following her graduation, we leave for our yearly family vacation back ...
CSI
SCOTT QUIMBY

Over the first three Securing Active Directory webinars, we have covered a lot of ground. If you haven't watched ...
CSI
SCOTT QUIMBY
Would you like a more organized, hardened environment considering today's threat landscape? What actions can you ...
CSI
SCOTT QUIMBY

"A chain is only as strong as its weakest link"
-Thomas Reid, "Essays on the Intellectual Powers of Man" - 1786
The SolarWinds ...
CSI
SCOTT QUIMBY

"A chain is only as strong as its weakest link"
-Thomas Reid, "Essays on the Intellectual Powers of Man" - 1786
The SolarWinds ...
CSI
SCOTT QUIMBY
Today we continue our look at a series of practical steps that districts can use to increase their NIST compliance. Looking ...
CSI
SCOTT QUIMBY

There is nothing more important than keeping your district and staff and students safe. Cybersecurity is not a topic that you can simply ...
CSI
SCOTT QUIMBY

Today's NIST topic is data recovery. The most obvious example of meeting this NIST standard is maintaining good backups. This ...
CSI
SCOTT QUIMBY

It has always been a challenge to provide adequate technical staffing to support both teaching and learning and the back-end administrative functions ...
CSI
SCOTT QUIMBY

Today we continue our look at a series of practical steps that districts can use to increase their ...
CSI
SCOTT QUIMBY

Today we continue our look at a series of practical steps that districts can use to increase their ...
CSI
SCOTT QUIMBY
Today we continue our look at a series of practical steps that districts can use to increase their NIST compliance. Looking ...
CSI
SCOTT QUIMBY

This week's NIST TechTidbit is: Maintenance, Monitoring and Analysis of Audit Logs / DETECT.. Activate Audit Logging ...
This ...
CSI
SCOTT QUIMBY

Today we continue our look at a series of practical steps that districts can use to increase their ...
CSI
SCOTT QUIMBY

Controlled Use of Administrative Privileges / DETECT / PROTECT..Change Default Passwords..Ensure the Use of Dedicated Administrative ...
CSI
SCOTT QUIMBY
Today we continue our look at a series of practical steps that districts can use to increase their NIST compliance. Looking ...
CSI
SCOTT QUIMBY

As we continue our NIST series, I am going to take a moment and discuss inventory and control of software assets in the IDENTIFY ...
CSI
SCOTT QUIMBY

Today we start a new series where we will touch on a series of practical steps that districts can use to increase your NIST ...
CSI
SCOTT QUIMBY

Weekly Tech Tidbit - Guarding The Wall
"Son, we live in a world that has walls, and those walls have to be guarded by men ...
CSI
SCOTT QUIMBY

On Wednesday we had some power failures due to that high wind storm coming through the region. There isn't really anything to ...
CSI
SCOTT QUIMBY

"Clean up, clean up, everybody, everywhere, Clean up, clean up everybody do their share"
-Barney
That song has been stuck ...
CSI
SCOTT QUIMBY

"When it absolutely, positively has to be there overnight" - FedEx
As many of you know, Bob and I have been doing this for a while - 41 years in fact. ...
CSI
SCOTT QUIMBY

Last time I talked about making email safer. I focused on inbound email to your users and outbound encrypted emails. However, I neglected to say ...
CSI
SCOTT QUIMBY

Last week I talked about the importance of Cloud Backup in our new remote teaching and learning and back-office school environments.
This week I am ...
CSI
SCOTT QUIMBY

Disk encryption is growing in popularity as a means of better-securing laptops and desktops. Microsoft is offering BitLocker natively in Windows ...
CSI
SCOTT QUIMBY

For the last few years Microsoft has been talking about "Modern" this or "Modern" that. In the quest for improved security they are agressively trying ...
CSI
SCOTT QUIMBY

Every day I am talking to a school district remotely and the conversation goes something like this, "We can't get into our buildings" or "We have very ...
CSI
SCOTT QUIMBY

We are not doing our full April Tech Talk in our office due to the shutdown. However, we wanted to do a virtual get together and share Scott's ...
CSI
SCOTT QUIMBY

I constantly harp on denying the bad guys access to your network, and if they are inside already, denying lateral movement. At the last Tech Talk, I ...
CSI
SCOTT QUIMBY

We have spent two decades linking all sorts of servers and processes to Active Directory for "ease of use". Sadly ease of use now can also mean "ease ...
CSI
SCOTT QUIMBY

Cisco is trying to do their part during the Pandemic.
If you are a Cisco AMP, Cisco DUO, Cisco Umbrella, or Cisco AnyConnect client, Cisco is allowing ...
CSI
SCOTT QUIMBY

The reality of many K-12 school districts is that you either have handed out or are handing out laptops to teachers and critical staff to get through ...
CSI
SCOTT QUIMBY

As I write this on Tuesday, March 24, 2020, I do hope that this message finds you well and staying safe as we all adapt to our new normal under the COVID-19 ...
CSI
SCOTT QUIMBY

K-12 education has been turned upside down. Remote learning is obviously the term du jour. At the same time as we are figuring out what remote instruction ...
CSI
SCOTT QUIMBY

Scott Quimby will go back to basics and talk about best practices for cleaning up Active Directory. For many of you Active Directory is now ...
CSI
SCOTT QUIMBY

These have been extraordinary times for the world, our country, our school districts and our families. We are implementing remote learning plans and ...
CSI
SCOTT QUIMBY

Earlier this month, on March 2, NIST formalized a significant number of changes to its password recommendations as part of the final release of its updated ...
CSI
SCOTT QUIMBY

As part of our client school district's response for Corona virus preparedness, we see an uptick in requests for VPN access into the school district's ...
CSI
SCOTT QUIMBY

This morning I read the headline that a second New York school district has shutdown over Coronavirus concerns. The question becomes how does a school ...
CSI
SCOTT QUIMBY

We have all had at a flood of information come at us in the last nine months regarding ransomware, malware, and cyber security options from all different ...
CSI
SCOTT QUIMBY

Microsoft has announced they are tightening the security standards for LDAP communications on Microsoft Active Directory networks. This has huge implications ...
CSI
SCOTT QUIMBY

In the continuing quest to battle ransomware in our networks, as well as other types of malware, just this month (Jan 2020) the National Institute ...
CSI
SCOTT QUIMBY

Happy New Year! Unfortunately, there is no rest for the weary fighting the battle to keep everyone safe.
Today I read a couple of scary articles:
"Couple ...
CSI
SCOTT QUIMBY

As 2019 comes to a close, on behalf of everyone here at CSI, I would like to say thank you for entrusting us with your technology needs. We appreciate ...
CSI
SCOTT QUIMBY

Happy Holidays.
As we go through the last full school week before the holiday break, I have a couple of quick professional and personal thoughts:
...
CSI
SCOTT QUIMBY

The Cybersecurity news has been pretty depressing over the last week.
I read an article that a Cybersecurity insurance company is refusing to pay for ...
CSI
SCOTT QUIMBY

We have all heard the story of the Trojan Horse. The Greeks built it and left it in front of Troy. The Greek army left. The Trojans went outside ...
CSI
SCOTT QUIMBY

Note: The response to our CyberSecurity Event has been overwhelming. To accommodate everyone who wants to attend we have moved it to a much large ...
CSI
SCOTT QUIMBY

Bob and are now multiple years in discussing the same thing - how to improve your district's security footprint. For most of that time many ignored ...
CSI
SCOTT QUIMBY

Most of can easily agree that our IT universe has been dominated over the past several months by cybersecurity discussions as we daily (sometimes it feels ...
CSI
SCOTT QUIMBY

We have been having a lot of discussions about how to better protect against ransomware and other threats with the recent attacks that have happened in ...
CSI
SCOTT QUIMBY

This week’s Tech Tidbit is shorter on my thoughts and words since the attached link below contains lots of reading on its own.
For the start of the ...
CSI
SCOTT QUIMBY

Over the past few years, we have been recommending the use of switch stacks in all your MDF and IDF locations. This has been done to aid in simplifying ...
CSI
SCOTT QUIMBY

In my 20s I went to Tahiti and went on a sunset cruise on the famed "Liki Tiki". It was an amazing sunset. Hula girls, and music. Along the ...
CSI
SCOTT QUIMBY

Over the past few weeks, we have had a number of cases where support tickets needed to be opened to resolve issues where end-users were reporting “inability ...
CSI
SCOTT QUIMBY

A constant frustration of ours is ensuring "clean" backups. If you corrupt your data or have a server failure, we need to reliably get that data back. ...
CSI
SCOTT QUIMBY

Hopefully, you all had a relatively sane and productive summer. Security-related topics have been in the news for most of the summer with several ...
CSI
SCOTT QUIMBY

Just when you thought it was safe to move along to other technical topics, along comes Scott Quimby's Hardening Active Directory Part III to scare you ...
CSI
SCOTT QUIMBY

We harp on the fact that if you have *ANY* VPN, or remote access capabilities into your district, you *MUST* use a commercial SSL certificate and not ...
CSI
SCOTT QUIMBY

All of us at CSI are techs at heart. We love talking about technical topics. However, we do also sell products. As you go into finalizing your ...
CSI
SCOTT QUIMBY

Hopefully for most of you, this is old news, but I know how busy everyone gets, especially this time of year with the end of school coming upon us. ...
CSI
SCOTT QUIMBY

I was recently reading a security study that said that 25% of applications are unpatched for an entire year! As you approach the summer remember that ...
CSI
SCOTT QUIMBY

Now that we have shifted to predominantly remote workers and remote teaching and learning, we have a number of new challenges as well as increased threats.
Challenge ...
CSI
SCOTT QUIMBY

This tidbit is part three in a series on understanding some mechanisms available to you for protecting e-mail sent from your domain. We covered this ...
CSI
SCOTT QUIMBY

One of the most important principles of a good network design is accurate time. Windows time is a whole lot like the 1960s car clock - always drifting ...
CSI
SCOTT QUIMBY

This tidbit is part two in a series on understanding some mechanisms available to you for protecting e-mail sent from your domain. We covered this topic ...
CSI
SCOTT QUIMBY

We are so focused on our networks being breached and the bad guys gaining a foothold to steal our money and personally identifiable information that we ...
CSI
SCOTT QUIMBY

Bob and I have discussed over and over the need for improved public wireless configuration. Some of you have gotten the message. Sadly many have ...
CSI
SCOTT QUIMBY

The reality is that your network is under attack. We need to protect our servers. We need to protect our data. One way we do that is by not remoting ...
CSI
SCOTT QUIMBY

Do you know how secure you are from the outside world? Maybe you're new and inherited a network, or there has been so much churn over the years with ...
CSI
SCOTT QUIMBY

This tidbit is starting a series on understanding some mechanisms available to you for protecting e-mail sent from your domain. We covered this topic ...
CSI
SCOTT QUIMBY

Another short and sweet tidbit.
When you are installing software, updates, patches, etc., reboot your server. I can't tell you the number of times ...
CSI
SCOTT QUIMBY

I have been watching the Cisco AMP and Paladin CyberSentinel Managed Endpoint Detect & Respond consoles for a number of clients of late. One thing ...
CSI
SCOTT QUIMBY

This tidbit is a refresher on looking at Cisco Firepower Intrusion Event logs and daily reports. Specifically, I wanted to review for all of you again ...
CSI
SCOTT QUIMBY

One of the things we are quite proud of here at CSI despite the numerous network down stories over the years (many of them gruesome) we have never had ...
CSI
SCOTT QUIMBY

This one is short and sweet.
Once in a while we encounter equipment or software that you have purchased elsewhere, but you want CSI to actively support ...
CSI
SCOTT QUIMBY

Often we all don't get true clarity on the importance of certain issues until you are living them. That is why for instance Dutchess County BOCES attempts ...
CSI
SCOTT QUIMBY

Keeping up with my theme on DNS related posts, this week I will again reprise a post from over a year ago on the importance of implementing proper control ...
CSI
SCOTT QUIMBY
In the February Tech Talk Webinar entitled, "SCCM Troubleshooting Part II" Scott introduced the new Support Center for client troubleshooting ...
CSI
SCOTT QUIMBY

The US-CERT (Computer Emergency Response Team) recently gave a presentation on what China has been doing to hack anything they can hack with the goal ...
CSI
SCOTT QUIMBY

We constantly harp on all of you segregating third-party vendor equipment on to vendor VLANs. The purpose of that is to keep third-party vendor equipment ...
CSI
SCOTT QUIMBY

Last month on January 22nd the US Dept of Homeland Security took the unusual step of issuing Emergency Directive 19-01 to all Federal Agencies. The ...
CSI
SCOTT QUIMBY

We continue our discussion of your closets and dumb stuff that can really hurt you. In part III we look at "plan b" and "plan c" for what to do if the ...
CSI
SCOTT QUIMBY

Right about now most of us are getting fairly comfortable with our current 802.11ac Wave 2 wireless deployments. But as we all know technology, and ...
CSI
SCOTT QUIMBY

The February Tech Talk Webinar is SCCM Troubleshooting Part II. Scott will introduce the new Support Center for client troubleshooting which became ...
CSI
SCOTT QUIMBY

In part I we were talking about UPSes. In part II we are going to continue our MDF/IDF UPS theme.
I want you to physically audit the power situation ...
CSI
SCOTT QUIMBY

Happy New Year! I was heartened by the number of noisy UPSes there were over the holiday break as people were taking my advice and calibrating their ...
CSI
SCOTT QUIMBY

This tech tidbit is a reprise of a tidbit we sent out back in June of 2018. You may have missed this post back then as it was the end of the school ...
CSI
SCOTT QUIMBY

As 2018 comes to a close, on behalf of everyone at CSI I would like to say thank you for entrusting us with your technology needs. Unlike most of our ...
CSI
SCOTT QUIMBY

As we approach the holiday break it is time once again to remember some basic maintenance that should be done. On a day where there isn't any bad ...
CSI
SCOTT QUIMBY

The FBI came to visit us last week. No it wasn't an investigation. It was for CSI's 3rd annual Security Event. I have talked about the topic of ...
CSI
SCOTT QUIMBY

I am watching with some interest a growing trend with district’s implementing newer IP-based building systems (HVAC control, food service temperature ...
CSI
SCOTT QUIMBY

As you go through your normal yearly planning cycles remember that in January 2020 Microsoft will be retiring Windows Server 2008 R2, Windows 7, and Microsoft ...
CSI
SCOTT QUIMBY

In an Active Directory domain, we generally rely heavily on group policies. Microsoft best practices say that you should have at least two domain ...
CSI
SCOTT QUIMBY

This week's Tech Tidbit is short and sweet.
If you have a server or device that is internet facing, make sure you have a real, commercial SSL certificate ...
CSI
SCOTT QUIMBY

When all else fails we reach for the backups. However, increasingly the bad guys are consciously seeking out your backups and deleting them as part ...
CSI
SCOTT QUIMBY

One of the key features of the newest firewalls and intrusion protection systems (IPS) has been the addition of something called GeoBlocking. This feature ...
CSI
SCOTT QUIMBY

Trend Micro has stated many times that you have approximately 4 minutes between when a threat enters your network and the infection breaks out.
But ...
CSI
SCOTT QUIMBY

At some point in your life, you probably were locked out of something - your house, your car, your office. I am sure it was awful trying to figure out ...
CSI
SCOTT QUIMBY

Most of Google's products are free. The reason is that you are their product. Their computers read your emails. They send you targeted ads based ...
CSI
SCOTT QUIMBY

It is important to have accountability to the taxpayers independently proving that each school district has adequate financial controls in place and ...
CSI
SCOTT QUIMBY

I can't tell how many times I have heard from non-technical Mac people that, "they don't need anti-virus." The Apple person that sold them their Mac told ...
CSI
SCOTT QUIMBY

Recently I read an interesting article on malware development techniques. SentinelOne, Cisco AMP, and other antivirus products rely on the VirusTotal ...
CSI
SCOTT QUIMBY

We have to be constantly vigilant to prevent malware, trojans, and other bad actors from taking root in our school networks to steal personally identifiable ...
CSI
SCOTT QUIMBY

The school year has started and we're anxious to update you on what our webinar, seminar, and Tech Talk schedule for the Fall and Winter.
Wednesday, ...
CSI
SCOTT QUIMBY

SCCM Configuration Manager is an amazing tool. But when things don't go as planned, that tool becomes immensely frustrating. Scott Quimby will walk ...
CSI
SCOTT QUIMBY

On Wednesday, October 3rd Cisco Meraki will be running a hands-on workshop where you can learn all about the new additions to Cisco Meraki's cloud-managed ...
CSI
SCOTT QUIMBY

Through our partnership with Synnex Corporation CSI is an approved vendor on the NCPA national purchasing contract which is a legal alternative for our ...
CSI
SCOTT QUIMBY

During our May Tech Talk meetings one of my summertime recommended tasks was for everyone to find and eliminate “zombie” servers. Zombie servers ...
CSI
SCOTT QUIMBY

When something goes sideways in our technical worlds some of the first questions we get asked, after “when is XXXX going to be back up”, is “what ...
CSI
SCOTT QUIMBY

**Note – Client tech directors in Dutchess County got a preview of this Tuesday so if you are in that group you may skip the rest of this note and go ...
CSI
SCOTT QUIMBY

We have been discussing a whole lot of security issues over this past year. Many of you are already moving forward to address many of our recommendations. ...
CSI
SCOTT QUIMBY

While we can never say, all is well in the world of network security, this week I feel I can write to you about something other than a US-CERT alert.
This ...
CSI
SCOTT QUIMBY

As I write this, Netflix is bringing back a new version of "Lost in Space". Hopefully, it is better than the movie and truer to the original series. ...
CSI
SCOTT QUIMBY

Well, it’s time for another Tech Tidbit from me and right on cue another alert from the National Cyber Awareness system run by the good people at the ...
CSI
SCOTT QUIMBY
The other day I was sitting in one of our Tech Talk presentations and Bob discussed the importance of Internet of Things (IoT) security. That made me ...
CSI
SCOTT QUIMBY

Many of you may be on the US-Cert alert e-mail list, but I suspect many of you are not. Since most all of you have Internet-facing devices, or even ...
CSI
SCOTT QUIMBY

We spend huge amounts of time thinking about server and workstation patches, firewall and switch patches and software patches, but when was the last time ...
CSI
SCOTT QUIMBY

One of the most confusing things we all encounter is Microsoft software licensing. You hear one explanation and then another. We are left mystified ...
CSI
SCOTT QUIMBY
CSI is excited to announce our third hands-on learning event entitled "Introducing Microsoft Teams for Next Generation Classroom Teaching and Learning" ...
CSI
SCOTT QUIMBY

CSI is pleased to announce that on Thursday, May 3rd from 8:30-4pm we will be hosting HPE Nimble in an all-day event. In the morning Nimble will ...
CSI
SCOTT QUIMBY

Preparing for "A rather blustery day"
"Oh the wind is lashing lustily
And the trees are thrashing thrustily
And the leaves are rustling gustily
So ...
CSI
SCOTT QUIMBY

"Configuring and Managing APC UPSes" was held on Tuesday, April 3rd at 10:30 am. One of the most valuable items in your data center and your network ...
CSI
SCOTT QUIMBY

Back on January 29th, there was a flurry of discussion in the IT world about the announcement from Cisco of an Adaptive Security Appliance (ASA) Remote ...
CSI
SCOTT QUIMBY

The call came in. We have a serious virus outbreak. Can you help?
Over the years we have been asked this question time and ...
CSI
SCOTT QUIMBY

The 2018 Yankees have taken the field. We'll all find out soon who is playing second and third base.
In the meantime, I want to continue ...
CSI
SCOTT QUIMBY

The Snort IPS engine is at the core of both the Cisco Firepower Threat Defense and Cisco Meraki IPS systems. Maintained by Cisco’s Talos Group, the ...
CSI
SCOTT QUIMBY

Now that the NFL season is over we turn our eyes to Valentines Day when Yankees Pitchers and Catchers report for Spring training. It ...
CSI
SCOTT QUIMBY

I wanted this week to take a few minutes to share with you our latest thinking on the Intel Spectre and Meltdown fiasco. In a nutshell, ...
CSI
SCOTT QUIMBY

One area of security we often overlook is that of the servers themselves. Most of our servers have some sort of remote access card built into them to ...
CSI
SCOTT QUIMBY

CSI and Microsoft are excited to present a Windows 10 in Education Deployment and Manageability Workshop on Wednesday, February 28th from 8:30-12pm. ...
CSI
SCOTT QUIMBY

One of the most frustrating things for users and the technical staff that support them is erratic email flow. Often users and staff don't know that ...
CSI
SCOTT QUIMBY

The requirements of K-12 are increasingly for anytime, anyplace learning as students use various devices both inside the district and at home. One ...
CSI
SCOTT QUIMBY

One of the most frustrating things for users and the technical staff that support them is erratic email flow. Often users and staff don't know that ...
CSI
SCOTT QUIMBY

Back in May 2015 we started talking about the Microsoft Group Policy security change to prevent a "man in the middle attack" where any Group Policy ...
CSI
SCOTT QUIMBY

Short but somewhat scary tidbit from me this week that serves as a reminder that there is a reason that the CSI team advocates:
1 – That we need multiple ...
CSI
SCOTT QUIMBY

You will find on our web site under Webinar recordings, Hardening Active Directory Part I and also Part II. If you haven't watched those presentations, ...
CSI
SCOTT QUIMBY

For years the best practice, and rules the most auditors hold IT departments to when it comes to secure password policies have included the following:
1 ...
CSI
SCOTT QUIMBY

Previously we talked about limiting the use of "local administrators" to improve the security of your network. However, we do actually need a local administrator ...
CSI
SCOTT QUIMBY

In this week’s Tech Tidbit I want to talk a bit about the importance of implementing proper control of DNS as part of your malware protection program.
DNS ...
CSI
SCOTT QUIMBY

In the real world, it’s no longer a matter of if an attacker will get in, but when and for how long. Is your district really prepared?
I am pleased ...
CSI
SCOTT QUIMBY

One of the most frustrating things for users and the technical staff that support them is erratic email flow. Often users and staff don't know that ...
CSI
SCOTT QUIMBY

I have been talking over the past year about "Hardening Active Directory". In those discussions, we have been talking about implementing a granular ...
CSI
SCOTT QUIMBY

The October Tech Talk meeting was jammed packed with information. There was more information than time allowed us to present.
Therefore, Scott ...
CSI
SCOTT QUIMBY

Welcome to the second installment of, "Weekly Tech Tidbits". This week I am going to answer a very common question, "Why do we have to remove local ...
CSI
SCOTT QUIMBY

Welcome to the inaugural edition of CSI’s “Your Weekly Tech Tidbit”. Building on Scott’s ever popular Tech Tidbits portion ...
CSI
SCOTT QUIMBY

The October Tech Talk meeting was jammed packed with information. There was more information than time allowed us to present.
Therefore, Scott ...
CSI
SCOTT QUIMBY

We wanted to let you know the CSI Tech Talk meeting and webinar dates for the 2017-2018 school year.
Our Tech Talk free knowledge transfer sessions ...
CSI
SCOTT QUIMBY

The reality is that your network is under attack. The bad guys are using advanced machine learning techniques to exploit sometimes subtle vulnerabilities ...
CSI
SCOTT QUIMBY

The next CSI Tech Talk Webinar entitled, "Hardening Active Directory and Group Policy Part II" is scheduled for Tuesday, September 19th at 10:30 am. ...
CSI
CSI

CSI is pleased to announce that our Federal GSA IT Schedule 70 contract has been renewed. This renewal came after an audit of compliance with the GSA ...
CSI
SCOTT QUIMBY

The reality is that your network is under attack. The bad guys are using advanced machine learning techniques to exploit sometimes subtle vulnerabilities ...
CSI
SCOTT QUIMBY

Reuters reports, "A bill proposed in Congress on Wednesday would require the U.S. National Security Agency to inform representatives of other government ...
CSI
SCOTT QUIMBY

Systems Affected
Microsoft Windows operating systems
Overview
According to numerous open-source reports, a widespread ransomware ...
CSI
SCOTT QUIMBY

The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology ...
CSI
SCOTT QUIMBY

Apple has released security updates to address vulnerabilities in multiple products. A remote attacker may exploit some of these vulnerabilities to take ...
CSI
SCOTT QUIMBY

Microsoft solution available to protect additional products
Today many of our customers around the world and the critical systems they depend ...
CSI
SCOTT QUIMBY

This is so cool. This guy really did save a big part of the world.
A 22-year-old British cybersecurity researcher thwarted yesterday's "Wanna Decryptor ...
CSI
SCOTT QUIMBY

LinkedIn Learning is offering free training until May 31st on some of Microsoft's newest technologies for developers. You can read about it here.
CSI
SCOTT QUIMBY

The summer months are often very busy times as we try to get all our projects accomplished before school starts again.
This month Scott Quimby will ...
CSI
SCOTT QUIMBY

Today Microsoft made some announcements regarding education. At the core of the announcements was the announcement of Windows 10 S on $189 laptops that ...
CSI
SCOTT QUIMBY

**NOTE: Due to ALL THE WINTER SNOW cancellations we pushed this final tech talk of the school year back one week**
Our Tech Talk quarterly, free knowledge ...
CSI
SCOTT QUIMBY

This month Scott Quimby continues his discussion of Microsoft Group Policy. He will focus on Microsoft Windows logon performance and reliability. There ...
CSI
SCOTT QUIMBY

This month Scott Quimby continues his discussion of Microsoft Group Policy. He will focus on Microsoft Windows logon performance and reliability. There ...
CSI
SCOTT QUIMBY

Scott Quimby continues his discussion of Microsoft Group Policy. He will focus on the different ways to deliver items to an end user's desktop. These ...
CSI
SCOTT QUIMBY

CSI is excited to announce that the folks from Cisco Meraki in California will be in our office to lead a discussion on the following Cisco Meraki Cloud ...
CSI
SCOTT QUIMBY

Our Tech Talk quarterly, free knowledge transfer session is Tuesday, March 14th (snow date Tuesday, March 21st) at 8:00 AM. This session is designed for ...
CSI
SCOTT QUIMBY

This month Scott Quimby continues his discussion of Microsoft Group Policy. He will focus on the different ways to deliver items to an end user's desktop. ...
CSI
SCOTT QUIMBY

**NOTE THE DATE HAS BEEN MOVED TO TUESDAY JANUARY 31st BASED UPON THE BAD WEATHER FOR THE MORNING. IF THE 24th DIDN'T WORK FOR YOU, PLEASE SIGN UP FOR ...
CSI
SCOTT QUIMBY
Paladin Sentinel Demo
CSI
SCOTT QUIMBY
CSI Tech Talk Windows 10
January 2017-Snow Day Edition
CSI
SCOTT QUIMBY
CSI January 2017 Tech Talk Snow Day Edition Tech Tidbits
CSI
SCOTT QUIMBY
CSI January 2017 Tech Talk Introduction to Microsoft AppLocker
CSI
SCOTT QUIMBY

Senior Systems Engineer and Microsoft MCSE Prayer Solanky presented an introduction to PowerShell.
Microsoft is increasingly moving towards command ...
CSI
SCOTT QUIMBY

This month Senior Systems Engineer and Microsoft MCSE Prayer Solanky will be presenting an introduction to PowerShell.
Microsoft is increasingly moving ...
CSI
SCOTT QUIMBY

Scott Quimby provides continues his discussion of Microsoft Group Policy. He will focus on a couple of important aspects of Group Policy:
Group ...
CSI
SCOTT QUIMBY

As your datacenters grow, your need for safe, reliable, fast shared storage grows. While the traditional workhorse Dell EqualLogic SANs are very good, ...
CSI
SCOTT QUIMBY

**Due to overwhelming demand Cisco has changed their plans and graciously agreed to hold a second Cisco Security session in the afternoon. The content ...
CSI
SCOTT QUIMBY

CSI is pleased to announce we are now a Nimble storage partner. We are also excited to be on the NYS contract PM20930
There is a critical need for ...
CSI
SCOTT QUIMBY

We are excited to be hosting two additional vendor informational seminar events in our office.
Tuesday November 15th 9:30-12pm - Cisco Security
...
CSI
SCOTT QUIMBY

**The date of this webinar has been changed from the 15th to the 14th to accommodate a very special Cisco Security Event on Tuesday November 15th. Look ...
CSI
SCOTT QUIMBY

Our Tech Talk quarterly, free knowledge transfer session is Tuesday October 18th at 8:00AM (snow date Tuesday October 25th). This session is designed ...
CSI
SCOTT QUIMBY

This month Scott Quimby will discuss Windows and Microsoft Office Activation. Microsoft activation can be a confusing topic and it isn't uncommon for ...
CSI
CSI

We hope that you are enjoying the end of your summer. We wanted to let you know the dates for both the CSI Tech Talk quarterly, ...
CSI
SCOTT QUIMBY

CSI is pleased to announce we are now a Nimble storage partner. There is a critical need for low cost, high speed, expandable, reliable storage. Nimble ...
CSI
SCOTT QUIMBY

CSI is pleased to announce that we are a Veeam authorized partner. CSI believes that Veeam Backup and Replication is the ideal way to backup and restore ...
CSI
SCOTT QUIMBY

CSI is pleased to announce that effective immediately we have been added to the NYS contract for APC by Schneider Electric products. CSI has always ...
CSI
SCOTT QUIMBY

I wanted to share with you one of the most vivid examples for why CSI's Paladin Sentinel approach to remote monitoring of your networks is superior to ...
CSI
SCOTT QUIMBY

There are many options for monitoring hardware and software for your network. Some are quite expensive and complex. Some are very simplistic. Some ...
CSI
SCOTT QUIMBY

Those of you who have worked with Bob and I since the early 80s know that we are all about free, knowledge transfer sessions to help you and your staff ...
CSI
SCOTT QUIMBY

CSI is pleased to announce the third of our Tech Talk webinar series on Tuesday June 7th at 10:30m. This is in addition to our quarterly Tech Talk ...
CSI
SCOTT QUIMBY

Our Tech Talk quarterly, free knowledge transfer session is Tuesday May 10th at 8:00AM. This session is designed for technical staff responsible for ...
CSI
SCOTT QUIMBY

This month Scott Quimby provides an overview of Microsoft Group Policy. Group Policy is Microsoft's preferred way to control the personality and many ...
CSI
SCOTT QUIMBY

CSI is pleased to announce the second of our Tech Talk webinar series on Tuesday April 19th at 10:30m. This is in addition to our quarterly Tech Talk ...
CSI
SCOTT QUIMBY

CSI is pleased to announce the beginning of our Tech Talk webinar series. This is in addition to our quarterly Tech Talk meetings. Our hope is that ...
CSI
CSI

We hope that you are enjoying your fall. We wanted to let you get a jump on your calendar reservations for the upcoming CSI Tech ...
CSI
SCOTT QUIMBY

CSI cordially invites you to join us for a Cisco Next Generation Cloud Networking Seminar. If you're considering an upgrade of your wireless infrastructure, ...
CSI
CSI

CSI is pleased to announce that we have been approved to offer additional products and services under our exisitng Federal GSA IT Schedule 70 contract. ...
CSI
CSI
For the third consecutive year, the Dutchess County Regional Chamber of Commerce is proud to partner with American Express to bring Small Business ...
CSI
SCOTT QUIMBY

When I was in High School at John Jay from 1974-1979, I took three computer classes: APL, Fortran, and BASIC. The computers in the entire High School ...
CSI
CSI

We hope that you are enjoying your summer. We wanted to let you get a jump on your calendar reservations for the upcoming CSI Tech ...
CSI
CSI

Webinar: Protect Yourself, Protect Your Patients
Failure to abide by HIPAA standards for technology compliance for ePHI can ...
CSI
CSI

March 4th Webinar: Protect Yourself, Protect Your Patients
Failure to abide by HIPAA standards for technology compliance for ePHI ...
CSI
CSI

Tech Talk is a quarterly, free knowledge transfer session that CSI offers four times a year. This session is designed for technical staff responsible ...
CSI
CSI

The Health Insurance Portability and Accountability Act (HIPAA) requirements makes privacy and security compliance for electronic Personal Health Information ...
CSI
CSI

The reality of today's world is that the internet can be a dangerous place. There are criminals trying to steal your money, your data, and your identity. ...
CSI
CSI

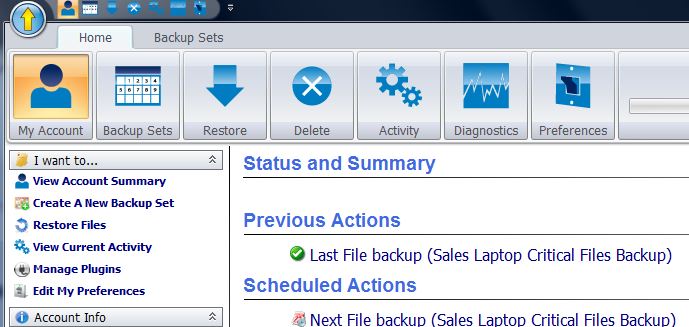
How do you backup your critical files? In talking to various users over the last 35 years for many organizations sadly the answer is, "Backup, what ...
CSI
CSI

CSI is pleased to announce that we have obtained a Federal GSA IT Schedule 70 contract for the following items:
CSI Professional IT Services
Paladin ...
CSI
CSI

The Health Insurance Portability and Accountability Act (HIPAA) requirements makes privacy and security compliance for electronic Personal Health Information ...
CSI
CSI

The reality of today's world is that the internet can be a dangerous place. There are criminals trying to steal your money, your data, and your identity. ...
CSI
CSI

How do you backup your critical files? In talking to various users over the last 35 years for many organizations sadly the answer is, "Backup, what ...
CSI
SCOTT QUIMBY

Click on January 2014 Tech Talk Quick Hits to listen to CSI's "Quick Hits" presentation. This was originally given in January of 2014 at our quarterly ...
CSI
CSI

One of the questions we often get from in-house IT staff is, "aren't you trying to replace me?". The answer to that question is NO. While CSI's ...
CSI
CSI

CSI is pleased to announce that we have obtained a Federal GSA IT Schedule 70 contract for the following items:
CSI Professional IT Services
Paladin ...
CSI
CSI

The Health Insurance Portability and Accountability Act (HIPAA) requirements makes privacy and security compliance for electronic Personal Health Information ...
CSI
CSI

The reality of today's world is that the internet can be a dangerous place. There are criminals trying to steal your money, your data, and your identity. ...
CSI
CSI

How do you backup your critical files? In talking to various users over the last 35 years for many organizations sadly the answer is, "Backup, what ...
CSI
CSI

If you have a family with children in sports, you probably occasionally struggle balance your personal and business responsibilities. In my case my ...
CSI
CSI

CSI is pleased to announce that we have obtained a Federal GSA IT Schedule 70 contract for the following items:
CSI Professional IT Services
Paladin ...
CSI
CSI

The Health Insurance Portability and Accountability Act (HIPAA) requirements makes privacy and security compliance for electronic Personal Health Information ...
CSI
CSI

The reality of today's world is that the internet can be a dangerous place. There are criminals trying to steal your money, your data, and your identity. ...
CSI
CSI

How do you backup your critical files? In talking to various users over the last 35 years for many organizations sadly the answer is, "Backup, what ...
CSI
CSI

At CSI we are constantly reading, learning, evaluating, and training on the latest technologies and best practices. I personally read at least 1,000 ...
CSI
CSI

CSI is pleased to announce that we have obtained a Federal GSA IT Schedule 70 contract for the following items:
CSI Professional IT Services
Paladin ...
CSI
CSI

I often ask the question to my staff and to vendors, "How do I know what I don't know?". By that I mean how do I find out about devices that are broken ...
CSI
CSI

CSI is pleased to announce that we have obtained a Federal GSA IT Schedule 70 contract for the following items:
CSI Professional IT Services
Paladin ...
CSI
CSI

Along with the Christmas shopping rush, business owners and managers are rushing to purchase computers, software and other IT equipment before the the ...
CSI
CSI

The Health Insurance Portability and Accountability Act (HIPAA) requirements makes privacy and security compliance for electronic Personal Health Information ...
CSI
CSI

The reality of today's world is that the internet can be a dangerous place. There are criminals trying to steal your money, your data, and your identity. ...
CSI
CSI

Why do so many things in our life break on holidays, nights, and weekends? Over the years I have had way too many pipes leak, hot water heaters spring ...
CSI
CSI

There are thousands of technology vendors and "IT guys". There are a few here and there who are quite good. However, there are many, many more that ...
CSI
CSI

A few months ago it wasn't a good morning for technology in our organization. First the text message came to me at 7:00 am stating that, "the office ...
CSI
CSI
For the second consecutive year, the Dutchess County Regional Chamber of Commerce is proud to partner with American Express to bring Small Business Saturday ...
CSI
CSI
The Health Insurance Portability and Accountability Act (HIPAA) requirements makes privacy and security compliance for electronic Personal Health Information ...
CSI
CSI
The reality of today's world is that the internet can be a dangerous place. There are criminals trying to steal your money, your data, and your identity. ...
CSI
CSI

Tech Talk is a quarterly, free knowledge transfer session that CSI offers four times a year. This session is designed for technical staff responsible ...
CSI
CSI
In today’s world we continue to push the concept of, “I want it now”. Anytime, anyplace data access is an increasing business requirement. ...
CSI
CSI
In today’s world we continue to push the concept of, “I want it now”. Anytime, anyplace data access is an increasing business requirement. ...
CSI
SCOTT QUIMBY

Click on October 2013 Tech Talk Quick Hits to listen to CSI's "Quick Hits" presentation. This was originally given in January of 2014 at our quarterly ...
CSI
CSI
We hope that you enjoyed your summer. With the start of the school year we are back to our normal schedules. We wanted to let you get ...
CSI
CSI
May 2013 Tech Talk Agenda and Registration Information
Tech Talk quarterly, free knowledge transfer session is just two weeks away on Monday May ...
CSI
CSI
https://bit.ly/XQUn6m
CSI
CSI
https://bit.ly/13M6Dtm
CSI
CSI
https://bit.ly/11ZkEAY
CSI
CSI
The gist is to mount the VMware Tools in VCENTER. Accept the warning that you can’t install this if the OS isn’t there. Go onto Windows Core ...
CSI
CSI
The Dutchess County Regional Chamber of Commerce IT Committee is presenting a seminar entitled "IT Security 101" on Tuesday May 14th from 8:30am-12pm ...
CSI
CSI
https://bit.ly/11ZmCRU
CSI
CSI
https://bit.ly/11ZmCRU
CSI
CSI
https://cnet.co/11ZmamM
CSI
CSI
https://bit.ly/11ZlPR5
CSI
CSI
https://on.mash.to/11ZlzkX
CSI
CSI
https://bit.ly/11ZklpO
CSI
CSI
https://bit.ly/11Zk3PN
CSI
CSI
https://bit.ly/11ZiQIf
CSI
CSI
The Dutchess County Regional Chamber of Commerce IT Committee is presenting a seminar entitled "IT Security 101" on Tuesday May 7th from 8:30am-12pm at ...
CSI
CSI
https://bit.ly/11ZleyB
CSI
CSI
https://bit.ly/11Zjs0C
CSI
CSI
https://bit.ly/11ZkSIi
CSI
CSI
https://bit.ly/11Zj6ai
CSI
CSI
https://bit.ly/11ZiyB0
CSI
CSI
https://bit.ly/11ZhT2w
CSI
CSI
https://bit.ly/WApJR4
CSI
CSI
https://bit.ly/WAppBO
CSI
CSI
https://onforb.es/13MaAOK
CSI
CSI
We have talked in recent weeks about how CSI's Paladin Remote Monitoring solution has saved a number of our larger clients from serious outages affecting ...
CSI
CSI
https://bit.ly/13MaiY8
CSI
CSI
https://bit.ly/13M9oel
CSI
CSI
https://bit.ly/13M9oel
CSI
CSI
https://bit.ly/13M5mCH
CSI
CSI
https://bit.ly/13M9932
CSI
CSI
https://bit.ly/UJXVIb
CSI
CSI
https://bit.ly/13M8VJd
CSI
CSI
https://bit.ly/YnNohE
CSI
CSI
https://bit.ly/XQIgpS
CSI
CSI
https://bit.ly/13M9Edj
CSI
CSI
https://bit.ly/13M8uyp
CSI
CSI
Despite not having Windows 7 "SP2", Microsoft just released a hotfix roll up which contains everything since SP1:
https://bit.ly/13Yq0zL
...
CSI
CSI
CSI's Paladin Remote Monitoring solution uncovered two major Exchange 2010 email crisises in the span of an hour on Wednesday. One affected a little ...
CSI
CSI
https://bit.ly/13M9Pp2
CSI
CSI
https://bit.ly/13M7Gtv
CSI
CSI
https://zd.net/13YoAoF
CSI
CSI
https://bit.ly/13Yp8uO
CSI
CSI
https://bit.ly/Z8Jb3Q
CSI
CSI
CSI's Paladin Remote Monitoring solution had an impressive save in the last couple of days.
Last week we had an ISP go on-site, after hours ...
CSI
CSI
Thankfully the re-scheduled CSI Tech Talk meeting happened on probably the nicest day of the Spring. The weather was great and the turn out was great ...
CSI
CSI
April 2013 Tech Talk Agenda and Registration Information
Tech Talk quarterly, free knowledge transfer session is just two weeks away on Tuesday, ...
CSI
CSI
https://bit.ly/13M86Qq
CSI
CSI
https://bit.ly/13M66YE
CSI
CSI
https://bit.ly/13Ys2zT
CSI
CSI
https://bit.ly/13YrQ3p
CSI
CSI
Exchange 2010 SP3:
Co-exists with Exchange 2013 CU1
Exchange 2010 can now be installed on Windows Server 2012
Exchange 2010 now supports Internet ...
CSI
CSI
https://bit.ly/13YqPIJ
CSI
CSI
https://bit.ly/13Yqiqm
CSI
CSI
https://bit.ly/15XgnAj
CSI
CSI
https://bit.ly/UK1Apm
CSI
CSI
https://bit.ly/XQHx8d
CSI
CSI
https://bit.ly/XQGLIx
CSI
CSI
https://bit.ly/XQGLIx
CSI
CSI
https://bit.ly/13YoM7q
CSI
CSI
https://bit.ly/XQGfKl
CSI
CSI
https://bit.ly/XQFO2R
CSI
CSI
https://bit.ly/WArmOw
CSI
CSI
https://bit.ly/XQFnp3
CSI
CSI
https://bit.ly/15XfhEM
CSI
CSI
https://bit.ly/15XeQtZ
CSI
CSI
https://bit.ly/XQE5dS
CSI
CSI
https://bit.ly/WAr765
CSI
CSI
https://bit.ly/WAqFER
CSI
CSI
https://bit.ly/13Ynj0Y
CSI
CSI
https://bit.ly/XQCZyN
CSI
CSI
https://bit.ly/15XfGad
CSI
CSI
https://bit.ly/15XdGii
CSI
CSI
https://bit.ly/XQVkf6
CSI
CSI
https://bit.ly/XQC3KM
CSI
CSI
https://tek.io/XQB8tK
CSI
CSI
https://bit.ly/XQUMFV
CSI
CSI
https://bit.ly/XQzrg3
CSI
CSI
https://bit.ly/XQTXwT
CSI
CSI
Due to the impending storm we are re-scheduling tomorrow's Tech Talk meeting to Tuesday April 9th. We are sorry for any inconvenience. Hopefully ...
CSI
CSI
https://bit.ly/XQAtsm
CSI
CSI
March 2013 Tech Talk Agenda and Registration Information
March 2013 Tech Talk quarterly, free knowledge transfer ...
CSI
CSI
https://bit.ly/15XemEi
CSI
CSI
https://bit.ly/13mieiH
CSI
CSI
https://bit.ly/XQz0SE
CSI
CSI
https://bit.ly/XQy8NT
CSI
CSI
https://bit.ly/XQTryY
CSI
CSI
https://bit.ly/XQT7jP
CSI
CSI
https://bit.ly/13Yrgme
CSI
CSI
https://bit.ly/XQSHKm
CSI
CSI
https://adobe.ly/13Yr3zF
CSI
CSI
https://bit.ly/XQwqwd
CSI
CSI
https://bit.ly/XQSdUs
CSI
CSI
https://bit.ly/XQRu5F
CSI
CSI
https://bit.ly/XQRSRz
CSI
CSI
https://bit.ly/XQRSRz
CSI
CSI
https://bit.ly/XQvo34
CSI
CSI
https://bit.ly/XQuP9J
CSI
CSI
https://bit.ly/XQR1Aj
CSI
CSI
https://bit.ly/XQQHBE
CSI
CSI
https://bit.ly/XQQjDa
CSI
CSI
https://bit.ly/XQtO1g
CSI
CSI
https://bit.ly/XOx1LR
CSI
CSI
https://bit.ly/15Xe7Jh
CSI
CSI
https://bit.ly/13mnH9l
CSI
CSI
I say this over and over. If you use any Google on-line product the government can ask for access to your information WITHOUT A WARRANT AND WITHOUT ...
CSI
CSI
https://bit.ly/WjNyfX
CSI
CSI
BSOD on Windows 7 64-bit: https://bit.ly/WAqj1f
CSI
CSI
https://bit.ly/XQPXwz
CSI
CSI
March 2013 Tech Talk Agenda and Registration Information
March 2013 Tech Talk quarterly, free knowledge transfer ...
CSI
CSI
https://bit.ly/XQPE4B
CSI
CSI
https://bit.ly/XQtcbS
CSI
CSI
March 2013 Tech Talk Agenda and Registration Information
March 2013 Tech Talk quarterly, free knowledge transfer ...
CSI
CSI
https://bit.ly/XQsQC0
CSI
CSI
https://bit.ly/XQPcnd
CSI
CSI
https://bit.ly/XQOWV5
CSI
CSI
https://bit.ly/XQOqGI
CSI
CSI
CSI's Paladin Remote Monitoring solution had a impressive save in the last couple of days. Last week we had an ISP going on-site, after hours to do a ...
CSI
CSI
https://bit.ly/XQsxaw
CSI
CSI
https://bit.ly/XQO16Y
CSI
CSI
https://bit.ly/XQO16Y
CSI
CSI
The following computers are affected by this issue:
Dell Inspiron N4120
Dell Inspiron N5110
Dell Vostro 3350
HP Pavilion DV6
HP Pavilion DV7
HP ...
CSI
CSI
https://bit.ly/XQNjqz
CSI
CSI
Mr. Grimes will be doing a program for PARENTS ONLY regarding internet awareness. Topics cover sexual predators, cyber bullying, identity theft, sexting, ...
CSI
CSI
https://bit.ly/XQMM7T
CSI
CSI
https://bit.ly/XQrUhd
CSI
CSI
Java 7 Update 17 and Java 6 Update 43: https://bit.ly/164gPwJ
CSI
CSI
https://bit.ly/XQMjTc
CSI
CSI
https://bit.ly/XQpLC2
CSI
CSI
https://onforb.es/XQrnvx
CSI
CSI
https://bit.ly/13mkkzb
CSI
CSI
https://bit.ly/UK1Apm
CSI
CSI
https://bit.ly/XOxmyi
CSI
CSI
https://bit.ly/XQM1M8
CSI
CSI
https://bit.ly/XQqTpm
CSI
CSI
https://bit.ly/XQLr0W
CSI
CSI
https://bit.ly/XQKYf5
CSI
CSI
https://bit.ly/XQKuG2
CSI
CSI
https://bit.ly/XQqqTX
CSI
CSI
https://bit.ly/UK3bLO
CSI
CSI
https://bit.ly/XQphMb
CSI
CSI
https://bit.ly/Ve37Ea
CSI
CSI
https://bit.ly/XQoI4Z
CSI
CSI
https://bit.ly/XQo73g
CSI
CSI
In 1978 I brought the first Apple II computer into John Jay High School in the Wappingers Central School District. It was the first PC ever in school. ...
CSI
CSI
https://bit.ly/WjMWHj
CSI
CSI
It seems like it has been just days since the last critical Adobe patches. Here's the latest Adobe Flash Security Update Advisory: https://adobe.ly/WjMclm
...
CSI
CSI
Internet Explorer 10 has been released. Microsoft has announced that they are starting to push IE10 automatic updates into all machines that have been ...
CSI
CSI
https://bit.ly/UK2B0q
CSI
CSI
https://bit.ly/XQnC9p
CSI
CSI
https://bit.ly/12SVpOT
CSI
CSI
https://bit.ly/XQjeas
CSI
CSI
https://bit.ly/UK0ZnE
CSI
CSI
https://bit.ly/XQmC5p
CSI
CSI
With the release of Exchange 2013 Microsoft has announced that you cannot upgrade directly from Exchange 2003 to Exchange 2013. Instead you must first ...
CSI
CSI
https://bit.ly/XQlyhC
CSI
CSI
https://bit.ly/UJZfL3
CSI
CSI
https://bit.ly/XQi2UE
CSI
CSI
https://bit.ly/12SCmEf
CSI
CSI
It is three weeks until CSI's March 2013 Tech Talk quarterly, free knowledge transfer session on Tuesday, March 19th at 8:00AM. This ...
CSI
CSI
https://bit.ly/XQJUIm
CSI
CSI
https://bit.ly/UJYxxd
CSI
CSI
https://bit.ly/XQJvWa
CSI
CSI
https://bit.ly/XQITji
CSI
CSI
https://bit.ly/12SWCWe
CSI
CSI
https://bit.ly/LhI10P
CSI
CSI
https://bit.ly/12SVUs8
CSI
CSI
https://bit.ly/Us8wap
CSI
CSI
https://bit.ly/12SQNbf
CSI
CSI
https://bit.ly/wHydwA
CSI
CSI
https://bit.ly/XQgxWy
CSI
CSI
https://bit.ly/Us7PxZ
CSI
CSI
https://bit.ly/MWdmnv
CSI
CSI
https://bit.ly/Us7kDU
CSI
CSI
https://reut.rs/12SUfTf
CSI
CSI
https://bit.ly/12SSYMc
CSI
CSI
https://bit.ly/YnNMwt
CSI
CSI
https://bit.ly/UJXwVT
CSI
CSI
https://bit.ly/YnNd5X
CSI
CSI
https://bit.ly/12SShCs
CSI
CSI
https://bit.ly/Us62ZN
CSI
CSI
https://bit.ly/MifA22
CSI
CSI
Today Apple released an update to address both the recent Exchange calendar issues and the battery drain issues for iPhones and iPads. I have upgraded ...
CSI
CSI
https://bit.ly/LhJQeh
CSI
CSI
https://bit.ly/LmzNmb
CSI
CSI
https://bit.ly/Us6uXU
CSI
CSI
https://bit.ly/Us5gvC
CSI
CSI
https://bit.ly/12SGm7F
CSI
CSI
https://bit.ly/Us3XwI
CSI
CSI
https://tek.io/Us3jj0
CSI
CSI
https://bit.ly/12SFfor
CSI
CSI
https://zd.net/12SBxLC
CSI
CSI
https://bit.ly/Us6V4t
CSI
CSI
https://bit.ly/Us5CT7
CSI
CSI
https://bit.ly/XQho9M
CSI
CSI
https://tnw.co/Us4IWL
CSI
CSI
The issue between Apple iPhones and iPads running IOS 6.1 and Microsoft Exchange 2010 has been narrowed down even further. It apparently specifically ...
CSI
CSI
https://onforb.es/Us2EOg
CSI
CSI

CSI is pleased to announce that we have obtained a Federal GSA IT Schedule 70 contract for the following items:
CSI Professional IT Services
Paladin ...
CSI
CSI
https://bit.ly/Ul037k
CSI
CSI
https://zd.net/UkZNFf
CSI
CSI
https://bit.ly/UkZvhG
CSI
CSI
https://on.mktw.net/UkZ8Uk
CSI
CSI
https://bit.ly/UkYVAw
CSI
CSI
https://bit.ly/UkYDtz
CSI
CSI
This is an awesome Microsoft site which allows you to examine what Group Policies: https://bit.ly/UkY7M4
CSI
CSI
https://bit.ly/UkXl1N
CSI
CSI
https://bit.ly/UkXl1N
CSI
CSI
https://bit.ly/UkXbrc
CSI
CSI
https://bit.ly/UkWYEa
CSI
CSI
https://bit.ly/UkXKky
CSI
CSI
https://bit.ly/UkWzlo
CSI
CSI
https://bit.ly/UkWzlo
CSI
CSI
VisiCalc was the "killer app" that launched Apple. It was strategically huge for IBM to get it converted to the original IBM PC. Long ago on a Saturday ...
CSI
CSI
ftp://ftp.adobe.com/pub/adobe/acrobat/win/11.x/11.0.00/misc/CustWiz11000_en_US.exe
CSI
CSI
https://bit.ly/SMz0yB
CSI
CSI
https://bit.ly/QC8tIg
CSI
CSI
https://bit.ly/QC6BiJ
CSI
CSI
https://bit.ly/QC6m7j
CSI
CSI
https://cnet.co/QC60Oa
CSI
CSI
https://fxn.ws/QC5Aao
CSI
CSI
https://bit.ly/QC52RX
CSI
CSI
https://bit.ly/QC4DyZ
CSI
CSI
https://bit.ly/QC4lIv
CSI
CSI
https://bit.ly/QC3RlA
CSI
CSI
https://bit.ly/QC3pnr
CSI
CSI
https://bit.ly/10MqkgB
CSI
CSI
https://bit.ly/J4dvmG
CSI
CSI
https://selnd.com/10MlOP0
CSI
CSI
https://bit.ly/10Ml10y
CSI
CSI
https://bit.ly/10MsxZa
CSI
CSI
This seems s pretty harsh opening position by HP not to support HP Windows 8 machines downgraded to Windows 7: https://bit.ly/10Mk2NX
CSI
CSI
https://bit.ly/10Mmwf5
CSI
CSI
https://tcrn.ch/10MhOxU
CSI
CSI
https://pojonews.co/10MrDfo
CSI
CSI
https://bit.ly/10MgivL
CSI
CSI
https://bit.ly/SMA19T
CSI
CSI
One opinion on the new operation system from Microsoft: https://bit.ly/10Mjck5
CSI
CSI
https://bit.ly/SMz0yB
CSI
CSI
https://bit.ly/SMyqAU
CSI
CSI
trib.al/s2igVR
CSI
CSI
https://bit.ly/SMxnRx
CSI
CSI
https://huff.to/SMwAQv
CSI
CSI
https://bit.ly/VSvhWp
CSI
CSI
https://bit.ly/VSvhWp
CSI
CSI
bit.ly/L4JT03
CSI
CSI
bit.ly/MUBPuO
CSI
CSI
https://bit.ly/VStCjI
CSI
CSI
https://bit.ly/VSsYCN
CSI
CSI
Dutchess County, NY was selected as the number one digital county in the 2012 Digital County Survey for counties with total populations of 250,000-499,00: https://bit.ly/VSs35f
...
CSI
CSI
https://bit.ly/VRTkoc
CSI
CSI
https://bit.ly/VRLcnU
CSI
CSI
As Hurricane Sandy approaches New York, CSI is actively watching our 24x7x365 Paladin Monitoring service to help our clients prepare their computers ...
CSI
CSI
https://bit.ly/VRSOqo
CSI
CSI
On Wednesday I was a guest panelist at the Dutchess County Regional Chamber of Commerce Business Expo 2012 in their "Ask a Geek" forum. One of the ...
CSI
CSI
CSI's October 2012 Tech Talk quarterly, free knowledge transfer session is tomorrow on Tuesday, October 23rd at 8:30AM. This session is designed ...
CSI
CSI
https://bit.ly/xrzmyh
CSI
CSI
I had a very strange iPad incident today. I was using my iPad to take notes while building some servers. I have the magnetic cover for my iPad2. ...
CSI
CSI
https://bit.ly/xab1Q2
CSI
CSI
https://bit.ly/A9mEck
CSI
CSI
https://fxn.ws/AxSptm
CSI
CSI
I find it interesting that not a single Google Droid based device is on the ActiveSync list. I guess that is why we see Corporate Sync instead of ActiveSync ...
CSI
CSI
https://fxn.ws/FPOdXJ
CSI
CSI
https://bit.ly/z52FiI
CSI
CSI
https://bit.ly/FRTk9o
CSI
CSI
https://bit.ly/FRSSrE
CSI
CSI
https://bit.ly/FRSwRH
CSI
CSI
https://bit.ly/xG7yeh
CSI
CSI
https://bit.ly/zSLTDL
CSI
CSI
This is a first user experience with Windows 8 for a non-technical user. Was the "Start" button a bad thing? It seemed pretty obvious to me. Here's ...
CSI
CSI
https://bit.ly/FRQu42
CSI
CSI
https://reut.rs/FQjUBC
CSI
CSI
https://bit.ly/FRQaT0
CSI
CSI
https://bit.ly/xMkvzF
CSI
CSI
https://bit.ly/FRPVHB
CSI
CSI
https://bit.ly/rQYBB0
CSI
CSI
https://bit.ly/wKfUWW
CSI
CSI
A well designed wireless infrastructure is vital as the number of mobile workers and mobile devices increase in your environment. CSIwill help you design ...
CSI
CSI
A well designed wireless infrastructure is vital as the number of mobile workers and mobile devices increase in your environment. CSIwill help you design ...
CSI
CSI
https://bit.ly/A39rGW
CSI
CSI
https://bit.ly/yezGUt
CSI
CSI
https://bit.ly/yaBHz3
CSI
CSI
https://bit.ly/xs00Zn
CSI
CSI
https://huff.to/zVcS5B
CSI
CSI
https://bit.ly/wPSpqY
CSI
CSI
https://bit.ly/wv2jrt
CSI
CSI
https://bit.ly/wXU9yn
CSI
CSI
https://bit.ly/xV7EnB
CSI
CSI
https://bit.ly/xxvdO8
CSI
CSI
https://bit.ly/zM0OWe
CSI
CSI
https://bit.ly/w9b36a
CSI
CSI
https://bit.ly/FQiuXF
CSI
CSI
https://bit.ly/xL2M8z
CSI
CSI
https://bit.ly/zStrGg
CSI
CSI
https://nyti.ms/wsm0EI
CSI
CSI
https://huff.to/AnHCwj
CSI
CSI
https://bit.ly/xWyY1d
CSI
CSI
https://bit.ly/A0ztQP
CSI
CSI
https://bit.ly/wbGtr8
CSI
CSI
https://bit.ly/zKdjsh
CSI
CSI
https://bit.ly/xxvdO8
CSI
CSI
https://bit.ly/zaf1Ea
CSI
CSI
https://adobe.ly/yhIAZX
CSI
CSI
https://bit.ly/zStrGg
CSI
CSI
https://bit.ly/zN7nil
CSI
CSI
The Calendar Checking Tool for Outlook (CalCheck) is a command-line program that checks Microsoft Outlook Calendars for problems. The tool opens an Outlook ...
CSI
CSI
https://bit.ly/ysqiew
CSI
CSI
https://bit.ly/z642gM
CSI
CSI
https://huff.to/AE2Ssp
CSI
CSI
https://huff.to/x3nLh1
CSI
CSI
https://huff.to/x3nLh1
CSI
CSI
https://bit.ly/zLZ2BP
CSI
CSI
https://bit.ly/ypmTJp
CSI
CSI
https://bit.ly/wLeuz9
CSI
CSI
https://bit.ly/w6G8Ga
CSI
CSI
https://bit.ly/xJwIpm
CSI
CSI
https://bit.ly/xIPaaO
CSI
CSI
https://bit.ly/zTX9SX
CSI
CSI
https://huff.to/xr9yIl
CSI
CSI
https://bit.ly/zagxAa
CSI
CSI
https://bit.ly/y1vdH7
CSI
CSI
https://bit.ly/yJUNgq
CSI
CSI
https://bit.ly/zH7DtB
CSI
CSI
https://bit.ly/zsKkQA
CSI
CSI
There is an on-line version of Microsoft Office with your iPad. Read about it here: https://bit.ly/AgBGwC
CSI
CSI
https://ind.pn/wmDu0R
CSI
CSI
https://bit.ly/AmbfcG
CSI
CSI
https://bit.ly/zQAkY7
CSI
CSI
https://bit.ly/zkV7DY
CSI
CSI
https://bit.ly/wCSuR8
CSI
CSI
https://bit.ly/xMmlAF
CSI
CSI
https://bit.ly/ygh4ZM
CSI
CSI
https://bbc.in/zzMB1T
CSI
CSI
https://bit.ly/wKfUWW
CSI
CSI
https://bit.ly/As8A0L
CSI
CSI
https://onforb.es/zWeoT2
CSI
CSI
https://bit.ly/w6FJc9
CSI
CSI
https://bit.ly/wiWiNo
CSI
CSI
https://bit.ly/ADvGgq
CSI
CSI
https://bit.ly/yaBHz3
CSI
CSI
https://bit.ly/AiSgu5
CSI
CSI
https://bit.ly/w5ub8j
CSI
CSI
https://tek.io/xdWRWh
CSI
CSI
https://bit.ly/zCfHaS
CSI
CSI
https://bit.ly/zwYbVD
CSI
CSI
https://bit.ly/zwYbVD
CSI
CSI
https://bit.ly/xMFN61
CSI
CSI
https://bit.ly/xhvK3P
CSI
CSI
https://bit.ly/ADI6hv
CSI
CSI
https://bit.ly/xm7v9B
CSI
CSI
https://bit.ly/xeRAfN
CSI
CSI
https://bit.ly/wNz0zS
CSI
CSI
https://bit.ly/yTJVog
CSI
CSI
This update has numerous Microsoft related updates to improve the integration with Microsoft servers and Active Directory. Some of the features include:
Improve ...
CSI
CSI
https://bit.ly/xb6dPG
CSI
CSI
https://bit.ly/zG81LY
CSI
CSI
https://bit.ly/AyLOq3
CSI
CSI
https://bit.ly/AxOomm
CSI
CSI
https://bit.ly/AgNid2
CSI
CSI
https://bit.ly/wGCcBq
CSI
CSI
https://on.wsj.com/xuXDbZ
CSI
CSI
https://bit.ly/yLi5ad
CSI
CSI
https://bit.ly/y4zhhV
CSI
CSI
https://bit.ly/wHXOLJ
CSI
CSI
https://bit.ly/yw8zKU
CSI
CSI
https://bit.ly/wU3kFj
CSI
CSI
I would venture to guess that most folks don’t know their external, public “hide” IP address. The way the internet works for every site you visit ...
CSI
CSI
https://bit.ly/yg5kRN
CSI
CSI
https://bit.ly/wo1if4
CSI
CSI
https://bit.ly/xcbzh0
CSI
CSI
https://bit.ly/w5eoie
CSI
CSI
https://bit.ly/zj6FPn
CSI
CSI
If you are a parent, you probably want to implement some basic web controls at home. OpenDNS is my first stop for this basic functionality. The basic ...
CSI
CSI
https://linkd.in/AlJSFJ
CSI
CSI
https://bit.ly/wgEZCb
CSI
CSI
https://bit.ly/ACHfZi
CSI
CSI
https://bit.ly/tBjIX8
CSI
CSI
https://bit.ly/yapUy3
CSI
CSI
Should you leave your computers on at night or shut them off when you go home?
The answer is "it depends".
There are many factors that go into this ...
CSI
CSI
https://bit.ly/wpPiyv
CSI
CSI
https://bit.ly/xOJqbV
CSI
CSI
https://bit.ly/x6S0jY
CSI
CSI
Wise words about technology and productivity: https://bit.ly/x8WwNP
CSI
CSI
https://bit.ly/wSS0U6
CSI
CSI
https://bit.ly/z9c5Nw
CSI
CSI
One of the questions I get a lot is how to send large files around. Previously I posted an article called "Share Files Via Dropbox Public Folder" that ...
CSI
CSI
https://bit.ly/zkV7DY
CSI
CSI
https://bit.ly/zYPXn1
CSI
CSI
https://bit.ly/wr3bea
CSI
CSI
https://bit.ly/rV4QM8
CSI
CSI
https://bit.ly/tXmfe0
CSI
CSI
https://bit.ly/uKxtm5
CSI
CSI
https://bit.ly/urc28I
CSI
CSI
Microsoft SQL databases have two components: Transaction Logs (.LDF) and Databases (.MDF). Transaction Logs are designed to keep track of each transaction ...
CSI
CSI
https://bit.ly/v8NvUz
CSI
CSI
https://bit.ly/xDBKdh
CSI
CSI
https://www.mypowerbag.com/
CSI
CSI
https://bit.ly/seDY5Y
CSI
CSI
https://bit.ly/rso6Fk
CSI
CSI
https://bit.ly/uojJEz
CSI
CSI
https://bit.ly/rFAnDq
CSI
CSI
https://bit.ly/taz94U
CSI
CSI
https://bit.ly/sfkgNQ
CSI
CSI
Active Directory Domain Services uses AdminSDHolder, protected groups and Security Descriptor propagator (SD propagator or SDPROP for short) to secure ...
CSI
CSI
https://bit.ly/uwVhtU
CSI
CSI
https://bit.ly/rxOVrQ
CSI
CSI
https://bit.ly/rPEH00
CSI
CSI
https://bit.ly/rBQWPC
CSI
CSI
https://bit.ly/uF2iH4
CSI
CSI
https://bit.ly/tryMCF
CSI
CSI
https://bit.ly/uyKif2
CSI
CSI
https://bit.ly/ty8pmv
CSI
CSI
https://bit.ly/rpBwew
CSI
CSI
I love Dropbox. I use this cloud service to connect my iPad2, iPhone, laptop, desktop, netbook, another desktop, Windows Home server, and my family's ...
CSI
CSI
https://bit.ly/rPT1me
CSI
CSI
https://bit.ly/u5QCBS
CSI
CSI
https://bit.ly/rytMyn
CSI
CSI
https://bit.ly/u4fSv4
CSI
CSI
https://bit.ly/rOK3OR
CSI
CSI
This move to TCP/IP IPv6 sounds like it will be extremely problematic for those focused on blocking spam: https://bit.ly/rBks2R
CSI
CSI
https://bit.ly/uuIxU5
CSI
CSI
https://bit.ly/vIQ3UE
CSI
CSI
https://bit.ly/uiyQ4Z
CSI
CSI
https://bit.ly/uFYP0i
CSI
CSI
https://bit.ly/s2UdwW
CSI
CSI
https://huff.to/u9sBea
CSI
CSI
There are numerous reports from major vendors that "spam" threats from unsolicited email have dropped substantially. The bad guys are shifting their ...
CSI
CSI
https://bit.ly/siJR8z
CSI
CSI
https://huff.to/tD49So
CSI
CSI
https://bit.ly/vjOP81
CSI
CSI
https://bit.ly/sD6EY4
CSI
CSI
Looking at this photo from 1956 I am reminded of the first Davong hard drive I saw for the IBM PC which was also 5MB and the size of a shoebox. Now ...
CSI
CSI
https://bit.ly/vQu760
CSI
CSI
https://bit.ly/rDtSbB
CSI
CSI
https://bit.ly/rWkqrC
CSI
CSI
https://tcrn.ch/v0yPdy
CSI
CSI
https://bit.ly/vuIpK0
CSI
CSI
https://bit.ly/v2gsL0
CSI
CSI
https://bit.ly/vtEdww
CSI
CSI
https://bit.ly/vtEdww
CSI
CSI
https://bit.ly/tHhcMQ
CSI
CSI
https://bit.ly/uU4XLm
CSI
CSI
https://bit.ly/rLrKpo
CSI
CSI
https://bit.ly/t1qQia
CSI
CSI
https://bit.ly/tB0nSR
CSI
CSI
https://bit.ly/sJcFTi
CSI
CSI
https://bit.ly/vefU2c
CSI
CSI
Microsoft SQL Server 2008 R2 increases the free SQL Server Express database size from 4GB to 10GB. This means that theoretically the free version of ...
CSI
CSI
https://bit.ly/rubMJJ
CSI
CSI
https://zd.net/tMFeS4
CSI
CSI
There are numerous reports from major vendors that "spam" threats from unsolicited email have dropped substantially. The bad guys are shifting their ...
CSI
CSI
https://bit.ly/rBwHxs
CSI
CSI
https://bit.ly/ujw5GS
CSI
CSI
Many technology hardware and software vendors take a very hard-line on support contracts. No support or maintenance contracts means no support. Some ...
CSI
CSI
https://bit.ly/tBjIX8
CSI
CSI
https://bit.ly/tBjIX8
CSI
CSI
https://bit.ly/uNvjFY
CSI
CSI
https://bit.ly/vxAmB9
CSI
CSI
https://bit.ly/rQYBB0
CSI
CSI
https://bit.ly/tVB5m1
CSI
CSI
Cloud data backup is a growing option for many users. The question that often comes up is how much bandwidth is considered adequate for cloud backup ...
CSI
CSI
https://bit.ly/tTNJbU
CSI
CSI
https://bit.ly/rTTVDh
CSI
CSI
https://bit.ly/tbSuRU
CSI
CSI
https://bit.ly/u5ApaI
CSI
CSI
https://tiny.cc/hkg6x
CSI
CSI
https://bit.ly/rFtjbp
CSI
CSI
https://bit.ly/tQCRTO
CSI
CSI
A well designed rack environment would include cold aisles (in front of the equipment with the AC vents) and hot aisles (behind the equipment with the ...
CSI
CSI
https://bit.ly/vFAx9U
CSI
CSI
https://bit.ly/tsJOgn
CSI
CSI
https://tiny.cc/hneje
CSI
CSI
https://huff.to/t6tvFo
CSI
CSI
https://bit.ly/vYHxm1
CSI
CSI
https://bbc.in/tQV804
CSI
CSI
https://bit.ly/tqwbBo
CSI
CSI
https://bit.ly/tqwbBo
CSI
CSI
https://zd.net/udVCmk
CSI
CSI
https://yhoo.it/rDlMp6
CSI
CSI
https://bit.ly/sxWiIK
CSI
CSI
https://bit.ly/vXaWuv
CSI
CSI
https://bit.ly/vs1YGz
CSI
CSI
https://tiny.cc/adrvh
CSI
CSI
https://huff.to/rxo4nf
CSI
CSI
https://bit.ly/sCp2fI
CSI
CSI
https://huff.to/v4Vn3x
CSI
CSI
https://bit.ly/vN4zmZ
CSI
CSI
https://bit.ly/txW08i
CSI
CSI
https://bit.ly/uQAugh
CSI
CSI
https://tiny.cc/d5pc8
CSI
CSI
https://bit.ly/sXg3RC
CSI
CSI
https://bit.ly/u4qhKV
CSI
CSI
https://bit.ly/sZUmTo
CSI
CSI
https://bit.ly/u1m8X8
CSI
CSI
https://bit.ly/tWNz3i
CSI
CSI
If you are a Microsoft Outlook user and are sending the same emails out with the same information over and over again, then you need to learn about Microsoft ...
CSI
CSI
https://bit.ly/ua3IOU
CSI
CSI
https://selnd.com/tU5sKk
CSI
CSI
https://bit.ly/sIpvr5
CSI
CSI
https://bit.ly/tE00F4
CSI
CSI
https://cnnmon.ie/vZDd2y
CSI
CSI
"Windows 7 clients experience a three to five second delay in obtaining an IP address through Dynamic Host Configuration Protocol (DHCP) at restart. This ...
CSI
CSI
https://bit.ly/vLqnjY
CSI
CSI
https://bit.ly/tj1pIQ
CSI
CSI
https://adobe.ly/u5CcO2
CSI
CSI
https://bit.ly/tUlKYl
CSI
CSI
https://bit.ly/uuRNGY
CSI
CSI
https://bit.ly/txLWyY
CSI
CSI
Microsoft has decided the time has come that everyone has to at least be at Internet Explorer 8 for all servers and workstations capable of being at Internet ...
CSI
CSI
DNS Islanding - I have been reading a series of technical threads on Microsoft DNS best practices. While we do follow DNS best practices for clients with ...
CSI
CSI
https://bit.ly/tDb5sx
CSI
CSI
https://bit.ly/ryPW6o
CSI
CSI
https://bit.ly/tjwdX9
CSI
CSI
https://bit.ly/t9dJP4
CSI
CSI
https://bit.ly/uQwpcm
CSI
CSI
https://adobe.ly/vW7DYy
CSI
CSI
https://bit.ly/vS11C0
CSI
CSI
https://bit.ly/vcx879
CSI
CSI
https://bit.ly/sxr8DF
CSI
CSI
https://huff.to/uQ1SKS
CSI
CSI
https://bit.ly/vxgxJu
CSI
CSI
https://bit.ly/uj5Lra
CSI
CSI
https://bit.ly/vYBb4C
CSI
CSI
https://bit.ly/sl2A5D
CSI
CSI
https://bit.ly/sk8BPK
CSI
CSI
https://bit.ly/rD4XUP
CSI
CSI
https://bit.ly/vQ0H64
CSI
CSI
https://bit.ly/vaFAy6
CSI
CSI
https://bit.ly/sOH3wo
CSI
CSI
https://linkd.in/v1oxP7
CSI
CSI
https://bit.ly/vgNUjV
CSI
CSI
https://bit.ly/trL0Gg
CSI
CSI
https://tiny.cc/vlb3f
CSI
CSI
https://tiny.cc/p937i
CSI
CSI
https://tiny.cc/u5ycq
CSI
CSI
https://tiny.cc/9wn0x
CSI
CSI
https://tiny.cc/61ez3
CSI
CSI
https://tiny.cc/9iybf
CSI
CSI
https://tiny.cc/8clc0
CSI
CSI
https://tiny.cc/1ryaz
CSI
CSI
https://tiny.cc/v9gqq
CSI
CSI
My wife is a heavy Outlook user. One of the problems I have is that we have a busy and complicate personal schedule around the kids. Who is doing ...
CSI
CSI
https://tiny.cc/26ahw
CSI
CSI
https://tiny.cc/sccd7
CSI
CSI
https://tiny.cc/sccd7
CSI
CSI
https://tiny.cc/fi2nw
CSI
CSI
Microsoft Outlook is quite versatile. It handles multiple email accounts. It is a reader for RSS subscriptions. It can be integrated with ...
CSI
CSI
https://tiny.cc/nu1db
CSI
CSI
https://tiny.cc/hm6g1
CSI
CSI
If you are like me, you have multiple email accounts. Microsoft Outlook can easily integrate multiple email accounts into your Outlook. You ...
CSI
CSI
https://tiny.cc/a4oo0
CSI
CSI
https://tiny.cc/o7fls
CSI
CSI
https://tiny.cc/xefej
CSI
CSI
https://tiny.cc/0q1ao
CSI
CSI
https://tinyurl.com/6s3yt2r
CSI
CSI
https://tiny.cc/xgc15
CSI
CSI
https://tiny.cc/rasto
CSI
CSI
https://tiny.cc/ggjwk
CSI
CSI
https://tiny.cc/3k04g
CSI
CSI
https://tiny.cc/ojgf3
CSI
CSI
https://tiny.cc/7cjuo
CSI
CSI
https://tiny.cc/i3rd4
CSI
CSI
https://tiny.cc/5b2dh
CSI
CSI
https://tiny.cc/pixg3
CSI
CSI
https://tiny.cc/52rb2
CSI
CSI
https://tiny.cc/ucmmk
CSI
CSI
https://tiny.cc/f45xu
CSI
CSI
https://tiny.cc/0yh4x
CSI
CSI
For serious breaches you should always seek guidance from law enforcement and computer professionals and perhaps your legal counsel on what your next ...
CSI
CSI
https://tinyurl.com/7jhl3zb
CSI
CSI
https://tiny.cc/livgm
CSI
CSI
You can now create your own business page on Google + - https://tiny.cc/vh2o2
CSI
CSI
https://tiny.cc/fjrkc
CSI
CSI
Interviewing is always a delicate topic. There are things you cannot legally ask. However, in the age of Facebook and Twitter, people freely post ...
CSI
CSI
https://tiny.cc/20g6e
CSI
CSI
https://tiny.cc/vtqt4
CSI
CSI
https://tiny.cc/qh3wj
CSI
CSI
https://tiny.cc/ryhy6
CSI
CSI
https://tiny.cc/ryhy6
CSI
CSI
https://tiny.cc/ryhy6
CSI
CSI
https://tiny.cc/ad1fe
CSI
CSI
https://tiny.cc/wa3am
CSI
CSI
https://tiny.cc/klou8
CSI
CSI
https://tiny.cc/acyez
CSI
CSI
https://tiny.cc/1a6ks
CSI
CSI
https://tiny.cc/wke8y
CSI
CSI
https://tiny.cc/t3k5g
CSI
CSI
When I was involved in a case with the US Secret Service, they brought in an "ethical hacker" as their computer consultant. One of the techniques ...
CSI
CSI
https://tiny.cc/1dazc
CSI
CSI
https://tiny.cc/vmx08
CSI
CSI
Here's an article about how "the cloud" is allowing startup businesses to implement affordable, scalable technology solutions that they most would not ...
CSI
CSI
Attempting to hack into bank accounts remains a major issue that banks face - https://tiny.cc/072nf
CSI
CSI
The internet can be the "Wild West". There are some pretty bad folks out there trying to steal your banking credentials or your identity. Some firms ...
CSI
CSI
A discussion of Google+ business pages vs. Facebook business pages - https://tiny.cc/m61nq
CSI
CSI
https://tiny.cc/nao3v
CSI
CSI
https://tiny.cc/2ww9d
CSI
CSI
Google Apps comes up a lot when "cloud" applications are discussed. This article points out Google's weaknesses in designing Office productivity software ...
CSI
CSI
This is the first contrarian article I have read about iPads not working out as an information gathering device in healthcare - https://tiny.cc/pz1vt ...
CSI
CSI
https://tiny.cc/0hkh8
CSI
CSI
https://tiny.cc/f4vm9
CSI
CSI
Dropbox is one of my favorite cloud based storage tools. I use it to connect my desktop, laptop, iPad2 and iPhone and share documents. I also use ...
CSI
CSI
Here's a discussion about both the Microsoft and Google cloud based email/collaboration environments - https://tiny.cc/3yoa4
CSI
CSI
https://tiny.cc/7gnnc
CSI
CSI
https://tiny.cc/91pal
CSI
CSI
https://tiny.cc/wf1vu
CSI
CSI
https://tiny.cc/wm5f7
CSI
CSI
Symantec has an interesting discussion on the problem of deleting IMG folders and contents. You can read it here.
CSI
CSI
Java has a critical Java 6 update 29 patch. I have been reading some commentary about issues with 6 update 29. Since Oracle has released Java 7, ...
CSI
CSI
Bring your own computer to work or school (BYOC) is a growing trend. More and more folks are wanting to bring their own laptops, tablets or smartphones ...
CSI
CSI
https://tiny.cc/z4w9b
CSI
CSI
https://tiny.cc/c2mw8
CSI
CSI
https://tiny.cc/7obod
CSI
CSI
https://tiny.cc/t6b7u
CSI
CSI
https://tiny.cc/vjnoj
CSI
CSI
https://tiny.cc/5xlip
CSI
CSI
https://tiny.cc/y575e
CSI
CSI
An interesting "Forbes" article on how Cloud computing is offering flexibility and scalability to startup businesses - https://tiny.cc/6fpbp
CSI
CSI
Thoughts on designing a modern business card - https://tiny.cc/1kh67
CSI
CSI
Add a logo to your QR code - https://tiny.cc/vrie3
CSI
CSI
A Google engineer writes what they think about Google + :https://tiny.cc/b5ao6
CSI
CSI
This is quite scary. Malware installed on your smartphone could record keystrokes on nearby keyboards: Read the article here: https://tiny.cc/6hpdu ...
CSI
CSI
Rumors were the Israeli's created the first virus that sought out and decimated the Iranian nuclear plant. Is this their second computer attack? ...
CSI
CSI
Here's the description of Exchange 2010 SP1 RU6: https://tiny.cc/hy1sw
CSI
CSI
In speaking with small business owners on a daily basis I have found that many of them have not put together either a short or long term plan for their company's ...
CSI
CSI
VMware has released some exciting performance data showing the improvements of ESXi 5.0 over ESXi 4.1 on the same hardware. You can read about their ...
CSI
CSI
The trade press is awash in negative Google articles. Here is one of them. I think the author's comments about "jeopardizing Google itself" are ...
CSI
CSI
VMware Thin App Factory sounds like a major step forward for VMware in the area of application virtualization. It is a new tool set that dramatically ...
CSI
CSI
Microsoft has created a very robust and expandable environment with Exchange 2010. You can add redundancy in a modular fashion. Data Availability ...
CSI
CSI
Malicious PDF Documents can be a threat to your business
I can't tell you how many people tell me that they never worry about clicking on Adobe PDF ...
CSI
CSI
The commander of the U.S. Cyber Command said Thursday that he does not favor giving the United Nations the power to regulate the Internet. You can read ...
CSI
CSI
Here is Adobe's official life cycle page listing what their support commitment is to their various products. Notice that Adobe 8 Reader went end of ...
CSI
CSI
If you have a corrupt recycle bin on your Windows 7 desktop, here is how you can fix it:
Click on the Start button
In the search box type: ...
CSI
CSI
A flaw was found in Adobe Flash that can allow a "clickjacking" exploit to turn on your webcam and microphone. Adobe is working on a fix. Networkworld ...
CSI
CSI
Anti-virus
We operate under a very simple “best practice” premise for anti-virus.
Workstations should have anti-virus that scans only the workstation ...
CSI
CSI
The National Security Agency (NSA) has suggested that security systems must be built with the assumption that there will be breaches. No matter how good ...
CSI
CSI
Printing for wireless users is often confusing
I have a laptop. I bring the laptop to work. It sits on our wireless network. My default printer ...
CSI
CSI
Microsoft TechNet discusses how to customize Office 2010 setup : https://tiny.cc/lks5i
CSI
CSI
We are celebrating our NEW office location in Fishkill with the Dutchess County Regional Chamber of Commerce. Please join us for an official ribbon cutting, ...
CSI
CSI
This could really mess things up in the coming months. We are already seeing this hit the distributors and limit what options we can offer. Read ...
CSI
CSI
Microsoft had a problem with Internet Explorer 9 and Outlook Web App 2010. It appears that Microsoft has resolved the issue in a recent Internet Explorer ...
CSI
CSI
https://tinyurl.com/5wgmn4p
CSI
CSI
The other day my credit card company's fraud unit called the house. They asked if I had made purchases at a Wal-Mart in Houston, Texas. I had not. ...
CSI
CSI
I remember my first computer experience on a 300 baud modem connected to a DEC terminal printer talking to Erie 1 BOCES in High School in 1974. ...
CSI
CSI
If you are looking to automate your Microsoft Office 2010 installs, check out this resource.
CSI
CSI
The Wall Street Journal has an excellent article on the reality that you may be the biggest security risk to your organization. CSI can help you assess ...
CSI
CSI
This article has an interesting alternative perspective on the Android vs. Apple IOS debate. Apple like RIM controls both the hardware and software which ...
CSI
CSI
There has been an interesting security change to Internet Explorer with cookies. A recent Internet Explorer 9 update improves security, but can confuse the ...
CSI
CSI
CDs and DVDs have a useful life of about 10 years. They are susceptible to failure just like previous tape media. This new technology says the ...
CSI
CSI
CDs and DVDs have a useful life of about 10 years. They are susceptible to failure just like previous tape media. This new technology says the ...
CSI
CSI
A recent Microsoft update to Internet Explorer 9 has disabled the ability to do FILE:// inside Internet Explorer. You can read about the change here. ...
CSI
CSI
For serious breaches you should always seek guidance from law enforcement and computer professionals and perhaps your legal counsel on what your next ...
CSI
CSI
https://www.networkworld.com/news/2011/091511-echoing-apple-microsoft-bans-flash-250943.html?source=NWWNLE_nlt_microsoft_2011-09-20
CSI
CSI
CSI offers some very affordable solutions for organizations of all sizes to protect against web surfing threats. Contact us if you'd like to talk about ...
CSI
CSI
This startup company wants to buy your excess CPU time. They are going to use it commercially using techniques similar to how excess CPU time is devoted ...
CSI
CSI
https://mashable.com/2011/10/05/tech-disabled/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed:+Mashable+(Mashable)
CSI
CSI
https://www.thinkgeek.com/gadgets/cellphone/e722/
CSI
CSI
https://www.msexchange.org/articles_tutorials/exchange-server-2010/management-administration/resource-mailboxes-exchange-2010-part1.html
https://blogs.technet.com/b/exchange/archive/2009/02/26/3407028.aspx
https://social.technet.microsoft.com/Forums/en-US/exchangesvrclients/thread/4bf5040b-b572-4aba-962d-78135593f44c
https://gallery.technet.microsoft.com/Exchange-2010-SP1-ExFolders-e6bfd405 ...
CSI
CSI
Specially formed images can be used to compromise the Blackberry environment. Research in Motion has a fix.
CSI
CSI
As the internet and the cloud is leveraged more and more it is no surprise that federal agencies are reporting a dramatic increase in cyber attacks. ...
CSI
CSI
Microsoft announced plans to release Service Pack 3 for Office 2007 and SharePoint Server 2007; it is expected to become available in Q4 2011.
https://blogs.technet.com/b/microsoft_mod_news_bites_blog/archive/2011/10/06/microsoft-office-2007-service-pack-3-announced.aspx ...
CSI
CSI
It is a 64-bit world. Novell won't offer updates beyond ZENworks 11 SP2 on any 32-bit OS platform.
https://www.novell.com/communities/node/13313/zenworks-and-32-bit-primary-server-support ...
CSI
CSI
As people and companies put more and more data into "the cloud" most people do not realize that due to the Electronic Communications Privacy Act of ...
CSI
CSI
Microsoft Volume Shadow Copy Service (VSS) is the underpinning of most Windows backup programs. It is also what is underneath Volume Shadow Copy which ...
CSI
CSI
https://blogs.computerworld.com/19074/five_reasons_companies_are_going_social_at_light_speed
CSI
CSI
https://virtualizationreview.com/blogs/virtual-insider/2011/10/readers-chime-in-why-vsphere-is-king.aspx?m=2
CSI
CSI
Interviewing is always a delicate topic. There are things you cannot legally ask. However, in the age of Facebook and Twitter, people freely post ...
CSI
CSI
This is why there is such a push for IP v6.
CSI
CSI
Internet Explorer 9 64-bit isn't supported by GroupWise 8 Web Access. Instead use Chrome or Firefox. GroupWise 2012 will support Internet Explorer 9 64-bit. ...
CSI
CSI
https://www.inforum.com/event/article/id/320490/
CSI
CSI
Interesting technology to improve endpoint security.
https://m.gizmag.com/article/20154/?utm_source=Gizmag+Subscribers&utm_campaign=2d424517d9-UA-2235360-4&utm_medium=email ...
CSI
CSI
https://www.symantec.com/business/support/index?page=content&id=TECH4948&actp=SUBSCRIPTION
CSI
CSI
https://searchenginewatch.com/article/2117187/The-Fed-Plans-to-Monitor-Google-Twitter-Facebook
CSI
CSI
Another good article from Symantec on how to fix VSS component failures.
https://www.symantec.com/business/support/index?page=content&id=TECH70486&actp=SUBSCRIPTION ...
CSI
CSI
https://www.symantec.com/business/support/index?page=content&id=TECH163900&actp=SUBSCRIPTION
CSI
CSI
New features are coming to GroupWise 2012:
iPad support
Web access enhancements
Calendaring enhancements
Novell Vibe and Skype integrations
Information ...
CSI
CSI
An interesting commentary about cloud office applications.
CSI
CSI
It is reported that the iPhone's Siri interface can bypass your phone's security. There is apparently a fix for this. You can read the article here. ...
CSI
CSI
GroupWise sites who have Blackberry Enterprise Server should think about upgrading off of 4.1.7 to 5.0.x.
https://www.novell.com/communities/node/13343/heads-blackberry-users ...
CSI
CSI
"ASHRAE’s Design Considerations for Data and Communications Equipment Centers recommends relative humidity conditions between 40% and 55%, with an allowable ...
CSI
CSI
Backing up your data is such a critical issue. Your data is the life of your business. FEMA estimates that 40-60% of businesses never re-open after ...
CSI
CSI
An interesting article on federal concerns about migrating their data to the cloud due to cyber attacks: https://tiny.cc/ghnt8
CSI
CSI
In my 33 years of working with various technologies we go through this phase a lot. We see the promise of a new technology. We see the marketing hype ...
CSI
CSI
With the push for electronic medical records (EMR), one of the concerns is whether patient's medical records confidentiality will appear on-line like ...
CSI
CSI
The laws governing electronic communications are very antiquated. Many do not provide the Constitutional protections afforded to physical searches. ...
CSI
CSI
Verizon and VMware are addressing the issue of having a "personal" phone and then having a separate "work" phone. With this new technology you will ...
CSI
CSI
Cool facts about Office: 750M people use Office worldwide. It's installed on 1B computers & every version of Office has #MSWord.
CSI
CSI
This Networkworld article re-states from Microsoft what I stated in my "Steps you can take to improve the security and worker productivity on your computers ...
CSI
CSI
https://www.theatlanticwire.com/technology/2011/06/united-nations-wikileaks-internet-human-rights/38526/
CSI
CSI
Recently I wrote the post "Ensuring Maximum Stability of Blackberry Enterprise Server". Blackberry just had a very nice companion article on identifying ...
CSI
CSI
https://www.networkworld.com/community/blog/president-barack-obama-order-bolster-classifi
CSI
CSI
Here is a nice review of all the changes in Facebook as they relate to your privacy settings. If you use Facebook, it is worth reviewing this quick ...
CSI
CSI
When I was involved in a case with the US Secret Service, they brought in an "ethical hacker" as their computer consultant. One of the techniques ...
CSI
CSI
https://www.theatlantic.com/technology/archive/2011/09/the-clouds-my-mom-cleaned-my-room-problem/245648/
CSI
CSI
https://www.novell.com/communities/node/13289/groupwise-mobility-kill-pill
CSI
CSI
https://www.novell.com/communities/node/13288/changing-groupwise-mailbox-capacity
CSI
CSI
Not exactly a kind review of Siri. I've read a lot of similar commentary over the last few days.
https://www.marketwatch.com/story/testing-siri-your-iphone-assistant-2011-10-14?siteid=nbch ...
CSI
CSI
I have seen a bunch of articles on this in the last few days as well. My personal experience was that my iPhone4 and my iPad2 both updated fine on the ...
CSI
CSI
https://www.wired.com/dangerroom/2011/10/virus-hits-drone-fleet/
CSI
CSI
https://www.novell.com/communities/node/13218/groupwise-groupwise-802-hp3-ships
CSI
CSI
This very humorous video illustrates that the world is now different.
https://www.linkedin.com/news?actionBar=&articleID=840203633&ids=0RejkQe38Md3wIe3gUd3APcjgUb3cPdzcMcz0Qe2MVd3oRdPcMd3wIe3gVe3APcjgU&aag=true&freq=daily&trk=eml-tod-b-all-96&ut=1OeXnDBUqXm4Y1 ...
CSI
CSI
IBM Corp. sold the IBM PC Co. to Lenovo when they exited the PC business. Now they say Lenovo is the number two PC manufacturer. Lenovo continues ...
CSI
CSI
In March 1980 I was 18 years old. I went with my dad to the West Coast Computer Faire at Moscone Center in San Francisco. There I was sitting at ...
CSI
CSI
I love my iPad2. Since I am such a proficient touch typist, I absolutely hate typing on my iPad. I have the luxury of having a small Netbook laptop that ...
CSI
CSI
Judging from my eight year olds extreme interest in iPad games, this should be a hit.
https://www.cultofmac.com/115973/disney-is-about-to-turn-your-ipad-into-an-interactive-game-board/ ...
CSI
CSI
The internet can be the "Wild West". There are some pretty bad folks out there trying to steal your banking credentials or your identity. Some firms ...
CSI
CSI
Interesting commentary from InfoWorld on iPad (aka Safari) browser use dramatically increasing despite Android devices having dramatically outsold iPads. ...
CSI
CSI
Finally an attempt to cut down on the charger plug clutter.
https://www.gizmag.com/apple-iphone-micro-usb-adapter/20094/picture/144394/
CSI
CSI
We have always loved Websense for content filtering of malicious web content. Now apparently Facebook does too for the same reasons.
https://www.computerworld.com/s/article/9220457/Facebook_turns_to_Websense_for_malicious_URL_detection?source=CTWNLE_nlt_pm_2011-10-03 ...
CSI
CSI
An interesting article discussing the fact that Microsoft Windows XP use is on the decline with just over 50% of the computers running Windows XP. At ...
CSI
CSI
Microsoft has put together a good list of basic things you, your employees and your family members should consider when using Social Media.
Protect your ...
CSI
CSI
Firefox continues to release updates at a dizzying pace. I read one article that they said they were going to continue to use numbers for their versions. ...
CSI
CSI
I love my Kindle. I actually read books again. Its battery life is amazing. The fact that I can go outside and read in bright sunlight is awesome. ...
CSI
CSI
This is an excellent article from Microsoft TechNet on the navigating complexities of DNS scavenging. DNS scavenging is a means of helping DNS clean ...
CSI
CSI
A brief article on the importance of listing your volunteer work on your resume or on-line profiles in addition to your work experience.
CSI
CSI
Microsoft made a big deal about desktop gadgets when Microsoft Vista came out. I never really liked them because they took up too much space on the desktop ...
CSI
CSI
Here is a post from Microsoft TechNet discussing issues with Microsoft Excel that have cropped up since MS11-072 came out and was applied. The article ...
CSI
CSI
Microsoft has been introducing the world to what is coming next in Windows 8. This is a good article introducing what comes after Windows 7:
https://www.infoworld.com/d/microsoft-windows/what-it-should-know-about-windows-8-173881?page=0,0&source=IFWNLE_nlt_daily_2011-10-01 ...
CSI
CSI
This is a great tip for setting Windows desktop wallpaper from Jeremy Moskowitz at GPAnswers.com. It is also a good example of leveraging the Group ...
CSI
CSI
While I'm sure this was accidental, it is one way to protect Internet Explorer's market share:
https://www.computerworld.com/s/article/9220435/Microsoft_kills_Google_Chrome_with_bad_malware_signature?source=CTWNLE_nlt_pm_2011-09-30 ...
CSI
CSI
A few months ago a number of our clients were surveyed in depth by a third party firm about what they thought about CSI. We are happy to report that ...
CSI
CSI
As Hurricane Irene approached New York, CSI used our 24x7x365 Paladin Monitoring service to help our clients prepare their computers and networks for ...
CSI
CSI
On September 6, 1979 my father and I entered the world of business opening the first store in the region dedicated to personal computers. I was ...
CSI
CSI
Malicious PDF Documents can be a threat to your business
I can't tell you how many people tell me that they never worry about clicking on Adobe PDF ...
CSI
CSI
Dead is still dead, but in Windows 8 the Blue Screen of Death (BSOD) will be friendlier "sad" face!
https://www.networkworld.com/community/blog/blue-screen-death-gets-new-life-windows-8 ...
CSI
CSI
QR Codes are those square bar codes you see popping up on billboards and advertising. If you have a smart phone and download a QR reader application, ...
CSI
CSI
With Google trying to break into the mainstream social networking market with Google Plus, Facebook has been busy with a number of changes of their own. ...
CSI
CSI
Here's an article from Novell on the features added to the new version of GroupWise coming in the fourth quarter. It sounds like there are some nice features ...
CSI
CSI
This is an excellent discussion of the impact Microsoft FSMO roles not being available on your Windows network:
https://jorgequestforknowledge.wordpress.com/2011/07/11/the-impact-of-fsmo-roles-not-being-available/ ...
CSI
CSI
I always liked Google Desktop and used it a lot. However, since Microsoft put a more robust desktop search function in Windows Vista and Windows 7, Google ...
CSI
CSI
Blackberry Enterprise Server (BES) functionality is highly dependent upon the following:
1 - Exchange being alive
2 - The controlling domain controller ...
CSI
CSI
When Exchange 2010 came out Microsoft stated that all the roles could be virtualized except for Unified Communications. As Exchange 2010 has been updated ...
CSI
CSI
In speaking with small business owners on a daily basis I have found that many of them have not put together either a short or long term plan for their company's ...
CSI
CSI
Since we have moved our office, I occassionally drive around the block for lunch at the local Panera Bread. There is always table after table of big ...
CSI
CSI
For our Novell GroupWise users here is an article from Novell talking about what is coming next (and not coming) for GroupWise.
https://www.novell.com/communities/node/13263/groupwise-retiring-technologies%E2%80%A6 ...
CSI
CSI
All of us who have an iPad or an iPhone or even PCs have struggled with the love/hate relationship between Adobe Flash and surfing the web. Flash has ...
CSI
CSI
From Adobe - "A Flash Player update is scheduled for release tomorrow, September 21, 2011. This update will address critical security issues in the product ...
CSI
CSI
An interesting article from Harvard Business Review on a research study that suggests having women in a group raises the team's collective intelligence ...
CSI
CSI
This is a pretty interesting article on how making scientific research into a computer game allowed on-line gamers to solve a scientific mystery that ...
CSI
CSI
Anti-virus
We operate under a very simple “best practice” premise for anti-virus.
Workstations should have anti-virus that scans only the workstation ...
CSI
CSI
Printing for wireless users is often confusing
I have a laptop. I bring the laptop to work. It sits on our wireless network. My default printer ...
CSI
CSI
Server and Workstation Clean Up Tips
Updates
Whether you are manually updating or refreshing your golden images, here are some things to consider:
Make ...
CSI
CSI
https://bit.ly/smyhod