So much has happened, and in some cases changed, since our April Tech Talk, that we felt our May webinar should be a Tech Talk Bonus edition. We will have a full cybersecurity update. We’ll say what we can about lessons learned in a new regional security event.

Tech Talk May Bonus Edition – Recording Available

Tech Tidbit – You need to keep attackers “Dazed and Confused” as they probe your network
“Been dazed and confused for so long…” -Led Zeppelin A former NSA Director said nearly a decade ago that we must start building systems, assuming the bad guys are sitting next to us in the room. We all glazed over that as we did all this beautiful integration “leveraging the directory” and designed elegant, well-thought-out […]
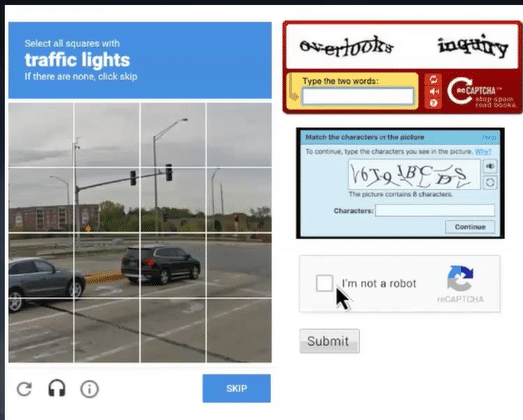
Tech Tidbit – Warning Fake Captcha Attacks Are Delivering Malware
As you present a better and better network defense, the bad guys continue to get more creative in their attacks. A new attack that has shot out of nowhere to instantly become very prevalent is the “Fake Captcha” attack. It is about two months old. Our partner SOCs report this as the new scam in […]

Tech Tidbit – The best defense may be a good offense
“The best offense is a good defense.” -Author Unknown “The best defense is to go on offense.” -Scott Quimby If you have been reading our Tech Tidbits over time, you know that a Security Operations Centers (SOCs) that provide 24x7x365 “eyes on glass” over your endpoints, or better still, over your entire network and firewalls, […]

Acture/CSI’s January Tech Talk – Recording Available
This exciting session will be led by Scott Quimby, CISSP, Senior Technical Advisor at Acture/CSI, and Larry Lanigan, Site Leader at Acture with 17 years of experience as a technology professional. What to Expect: 1. “Tech Tidbits” with Scott Quimby.

SentinelOne MITRE ATT&CK Enterprise 2024 Results – Recording Available
MITRE is a not-for-profit organization that operates federally funded research and development centers (FFRDCs) to provide technical expertise and innovative solutions to various U.S. government agencies. MITRE focuses on national defense, aviation safety, cybersecurity, healthcare, and more.

Tech Tidbit – My training day security event
I am sitting at my desk doing what I love—training Acture/CSI’s next generation of engineers. I am teaching them about Active Directory theory and operations. I am demonstrating how the Active Directory Recycle Bin works. I created a test ID in AD – Steve McQueen.

Tech Tidbit – Flash Drill – How Would Your Team Handle This Superintendent Request?
Today is a flash drill exercise. The Superintendent just told you that a retiring employee went rogue on the last day of school and sent a defamatory email to the entire district email distribution list. The Superintendent and your district legal counsel are asking you these questions: Where did the email go? Did it leave […]

Tech Tidbit – A discussion about insider threats
Acture/CSI has been going at a dizzying pace. I counted 16 online and in-person events for 2024, plus NYSCATE. Then you add all the Acture Solutions events. The Acture Solutions family has been busy providing you with the best technical information and best products to support you in maintaining a stable, secure, manageable network for […]

Tech Tidbit – Spring Break. I need only two things from you!
I am sticking you with real work for Spring Break. My list is very short. I need you to update, patch, and scan your servers and endpoints I need you to recalibrate all your APC UPSes. Remember to do it only on a nice calm day without weather or wind.

Tech Tidbit – I have a door problem at my house. You do too
I have a chronic issue with people’s ability to close doors securely. The issue is at home, and it spans all ages. I am constantly finding sliding doors ajar or the front door not closed. As some of you know I rescue English Springer Spaniels – aka bird dogs.

Tech Tidbit – Flash Drill – How Would Your Team Handle This Total Blindside Event?
Today is a flash drill exercise. The warm weather has arrived. It is Thursday afternoon of Memorial Day weekend, and the district gave back an unused snow day, making it a four-day weekend. The weather forecast is ideal. Everyone is bugging out to enjoy themselves.

Tech Tidbit – Your District Administration and Board Are Now Being Targeted In Ransomware Events
“Now, did you read the news today? They say the danger’s gone away. But I can see the fires still alight They’re burning into the night.” -Genesis, Land of Confusion As you continually upgrade your security posture and better protect your data from ransomware and data exfiltration, the bad guys keep devising innovative ways to […]

Tech Tidbit – About those inactive IDs
Do you know how many inactive accounts you have on your network? I know this can be a difficult number to determine sometimes. For most of you, Microsoft Active Directory is “the source of truth.” It syncs to Azure/Entra and/or Google Apps and elsewhere.

Tech Tidbit – Flash Drill – How Would Your Team Handle This Datacenter Event?
Today is a flash drill exercise. You are experiencing the blizzard of 2025. The Governor and County Executive have declared a state of emergency. The roads are closed. The snow keeps piling up. Your district data center is operational, and you have generator backup.

Tech Tidbit – Back from the dead Internet Explorer?
“And now for something completely different.” -Monty Python’s Flying Circus If you have been in the industry for a while, you have heard the warning, “Internet Explorer (IE) is dead. It is insecure. It has been retired. You must get off Internet Explorer and onto a more modern and secure browser.

Tech Tidbit – The Illusion of Logon Pages
“It Got Weird, Didn’t It?” -Austin Powers: The Spy Who Shagged Me I just attended the Huntress Security Event in NYC. It was at the Spy Museum on 8th Avenue (a cool place). I returned from that event to the office very afraid for all of us – myself included.

Tech Tidbit – The endgame plan for Windows 10
“This is the end, beautiful friend. This is the end.” -Jim Morrison of The Doors October 14, 2025, marks the end of the line for our tried-and-true, stable, and generally “good enough” Windows 10 OS. Windows 95, Windows XP, Windows 7, and Windows 10 have proven to be very stable OSes that we haven’t had […]
Introducing CSI’s CyberCNS Vulnerability Advisory Service Featuring ConnectSecure V4.0 – Recording Available
It seems like Cyber Attacks are happening everywhere these days. Whether it’s a national news report of an attack against a company that has your credit card information or local news reporting a school district like yours that’s been hit with a ransomware/data breach, these stories are plentiful.
Windows LAPS Configuration, Deployment, & Verification Webinar – Recording Available
LAPS is a powerful security tool built into Windows that you can use to secure local administrator accounts on your organization’s workstations and mitigate “pass-the-hash” attacks. In this hands-on webinar, Austin will talk about the theory behind LAPS and demonstrate live how to set it up from start to finish.

Acuture/CSI is hiring. Come join our growing family!
Acture/CSI is growing again. We are looking for high-quality individuals to work with our service delivery team. Please search our Acture/CSI online job database for opportunities in our Albany and Fishkill offices. Click here and add your resume to be considered for future employment: Acture Solutions Career Center.

CSI’s Special Update…Current K-12 Cybersecurity Challenges – Recording Available
Please join us on Wednesday, March 8th, as Scott Quimby delivers a special update addressing the current K-12 cybersecurity challenges, NIST Cybersecurity Framework (CSF) alignment as it relates to Ed Law 2-d, and NEW actions to improve your district’s security posture, help you with documentation, and measure your technology teams productivity.

Introducing CSI’s CyberCNS Vulnerability Advisory Service – Recording Available
It seems like Cyber Attacks are happening everywhere these days. Whether it’s a national news report of an attack against a company that has your credit card information or local news reporting a school district like yours that’s been hit with a ransomware/data breach, these stories are plentiful.
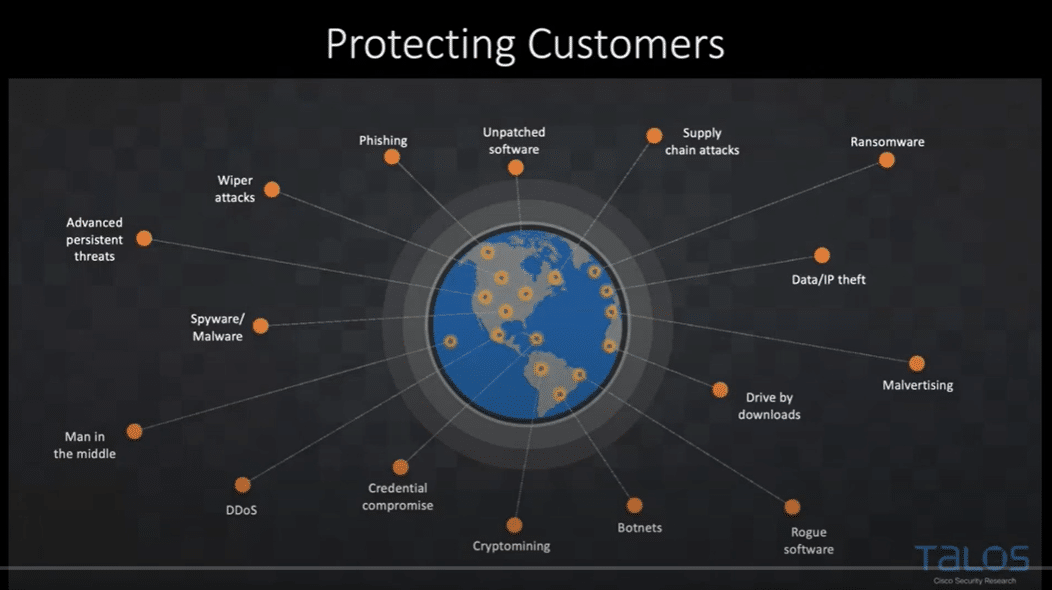
Cisco K-12 Cybersecurity Updates and Funding Ideas for Solutions – Recording Available
Join Cisco and CSI for a very special upcoming webinar. We will be joined by several specialists from Cisco (including Cisco Talos) who will discuss the dangers of spyware, deep links, content manipulation, malware, and keyloggers, and how to protect your school district from these threats.
Exclusive Cybersecurity Webinar with Acture/CSI and Blackpoint Cyber Experts – Recording Available
We are excited to invite you to an exclusive cybersecurity webinar recording led by industry experts at Blackpoint Cyber. This is your opportunity to gain insights from experts in cyber defense. Agenda: Introduction & Background of Blackpoint – Jamie Ivers, Senior Solutions Advisor SOC Overview – Jason Rathbun, Technical Director of Threat Operations SOC Saves: Real-World Examples – […]
