 As you present a better and better network defense, the bad guys continue to get more creative in their attacks. A new attack that has shot out of nowhere to instantly become very prevalent is the "Fake Captcha" attack. It is about two months old.
As you present a better and better network defense, the bad guys continue to get more creative in their attacks. A new attack that has shot out of nowhere to instantly become very prevalent is the "Fake Captcha" attack. It is about two months old.
Our partner SOCs report this as the new scam in town with rising attempts and results.
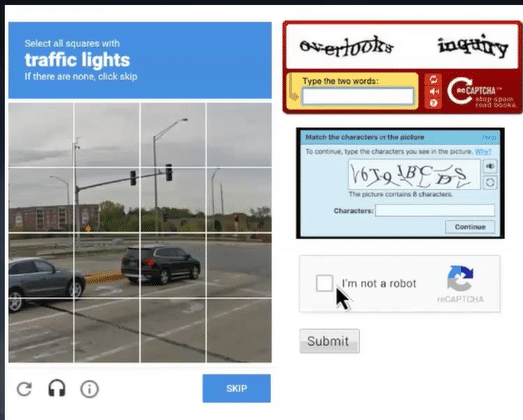
Fake Captcha relies on end users mindlessly clicking on "Are you a robot?" checkboxes. It is similar to MFA fatigue, where users just click yes to random MFA prompts instead of reading the screen and connecting the user's actions with whether or not they got an MFA prompt.
Captcha is generally associated with login or subscriptions. Random websites not associated with authentication are not where Captcha resides.
However, users just know they have to click and do the puzzle to get to what they want, so they automatically click away on the fake page. Down comes an info stealer from the malicious link.
We have seen this once. Of course, a "very" important user inside their district, holy of holies, was clicking on a malicious link. It looked like the VIP clicked on a malicious ad link for a very popular and respected "security" product!
The good news is that the district installed our CSEDR featuring SentinelOne Complete with the Vigilance SOC and our Huntress agents. Both SOCs immediately notified and intervened, killing the malware and isolating the host. Dead on contact, even though the user was tricked. Even though it was after hours, Christina and I were on the phone and making a post-event action plan within 5-10 minutes.
It's what we do.
Bad guys were killed, and the district was saved from some very bad activity.
Cool stuff. That's what our tools do 24/7 365.
A couple of parting thoughts:
- A real SOC with eyes on glass makes really good tools better
- EDR solutions protect even the most important users on the network from unknowingly doing potentially catastrophic things.
- The bad guys use SEO poisoning to get their malicious links into the top search positions.
- Because of all the SEO poisoning and paid ads that appear on my searches, I rarely use Google anymore. I use Microsoft Co-Pilot.
- You need to make sure no one—not your VIP users, not you, not your techs—has admin rights to the network or the workstation. Everyone must be a limited user—no exceptions.
- You need to add Fake Captcha to your Security Awareness Training immediately.
- The FBI strongly recommends that everyone have a good ad-block program on all their endpoints. I use AdBlock Pro, which has decent free and paid versions.
- You need to ensure you have DNS filtering in place and that it is filtering out known malware. We use Cisco OpenDNS (free) and Cisco Umbrella (fee).
- Acture/CSI lives in this world daily and has multiple high-level certified security engineers on staff (i.e., not just me).
- Acture/CSI also has incredible, world-class SOC and security analysts on speed dial—available 24/7 to support our in-house security team. (And yes, I have called at 1 a.m. on holidays with less than a 10-minute response time.)
We'd love to talk with you about your district's security posture and determine whether there is more you can do or if you can possibly explore reallocating your funds to produce a strong overall defense.
Give us a call. We'd love to discuss how to make your district safer.
-Scott Quimby, Senior Technical Advisor, CISSP
Acture/CSI

You must be logged in to post a comment.